Features
Pentest Robots – automate 80% of your manual pentesting work
Use Pentest Robots to automate tedious (but necessary) tasks so you can focus on quality results and complex issues - at scale.
Build visual testing flows tailored to your methodologies
Combine our tools with your logic for automated attack surface mapping
Retain full control over testing stages
Gain more time to deal with complex issues
Maintain testing consistency across teams and engagements
Getting Started
What are Pentest Robots?
TL;DR: Pentest Robots are software robots (bots) that orchestrate the tools on Pentest-Tools.com.
When you build a pentest robot, you design a testing flow that chains our tools based on your know-how and approach. The resulting robot is a testing flow you can run automatically (Scan with Robot) against any target you want.
Pentest robots pack an RPA-like approach which gives you the huge potential of automation without the risk of accidental damage. You retain full control over testing stages while injecting a massive efficiency increase into your workflow.
In the visual builder, drag & drop our tools and logic blocks to determine which pentest tools run and which types of findings trigger deeper, more focused scans. The visual flow is translated into a script that runs the tools automatically, giving you full visibility over progress and results.
Pentest robots require no coding, no maintenance, and you can run them no matter your platform. They also work just as well for simple and complex pentesting flows, so both junior and senior pentesters can use them. Tap into the large scalability potential they offer by automating 80% of your manual work (build all the robots you need, run multiple robots at the same time).
Why not use a vulnerability scanner instead?
Because they’re different types of tools.
| Vulnerability scanner | Pentest Robot |
|---|---|
| Automates repetitive, boring tasks that are part of any pentest - no maintenance required | Orchestrates multiple tools (incl. vulnerability scanners) |
| You can’t easily modify it to your needs | Runs custom testing flows adapted to your specific needs |
| It's very noisy because it attempts to find all vulnerabilities (it knows of) | Performs targeted testing by the conditioned tool execution on the matched filter/condition |
Offload 80% of manual pentesting work
Build pentest robots that do your work for you and eliminate repetitive tasks, waiting times, and manual steps included in every pentest.
| Do 80% less of this | And a lot more of this |
|---|---|
| Write custom scripts to chain tools | Find low hanging fruit you can report to clients and peers in minutes not hours days |
| Spend hours parsing results manually | Discover custom attack vectors |
| Make sure scanners worked as intended | Map more of the attack surface faster |
| Wait until one scanner finished to run the next one | Design complex pentesting flows you can use across engagements |
| Scavenge for interesting data in txt files | Combine tools and logic to automatically surface unusual findings |
| Spend too much time maintaining custom automation scripts | Chain vulnerabilities |
| Depend on specific frameworks to get high impact vulns | Adapt exploits and build new ones |
| Manually re run additional scans on the relevant data | Do post exploitation |
| Waste hours copy pasting from various docs in your reports | Use pivot techniques |
| Reuse elements and templates to export pro level reports |
Premades
3 Pentest Robots you can use right now
Run these pre-built, pre-tested robots as soon as you log into your account!
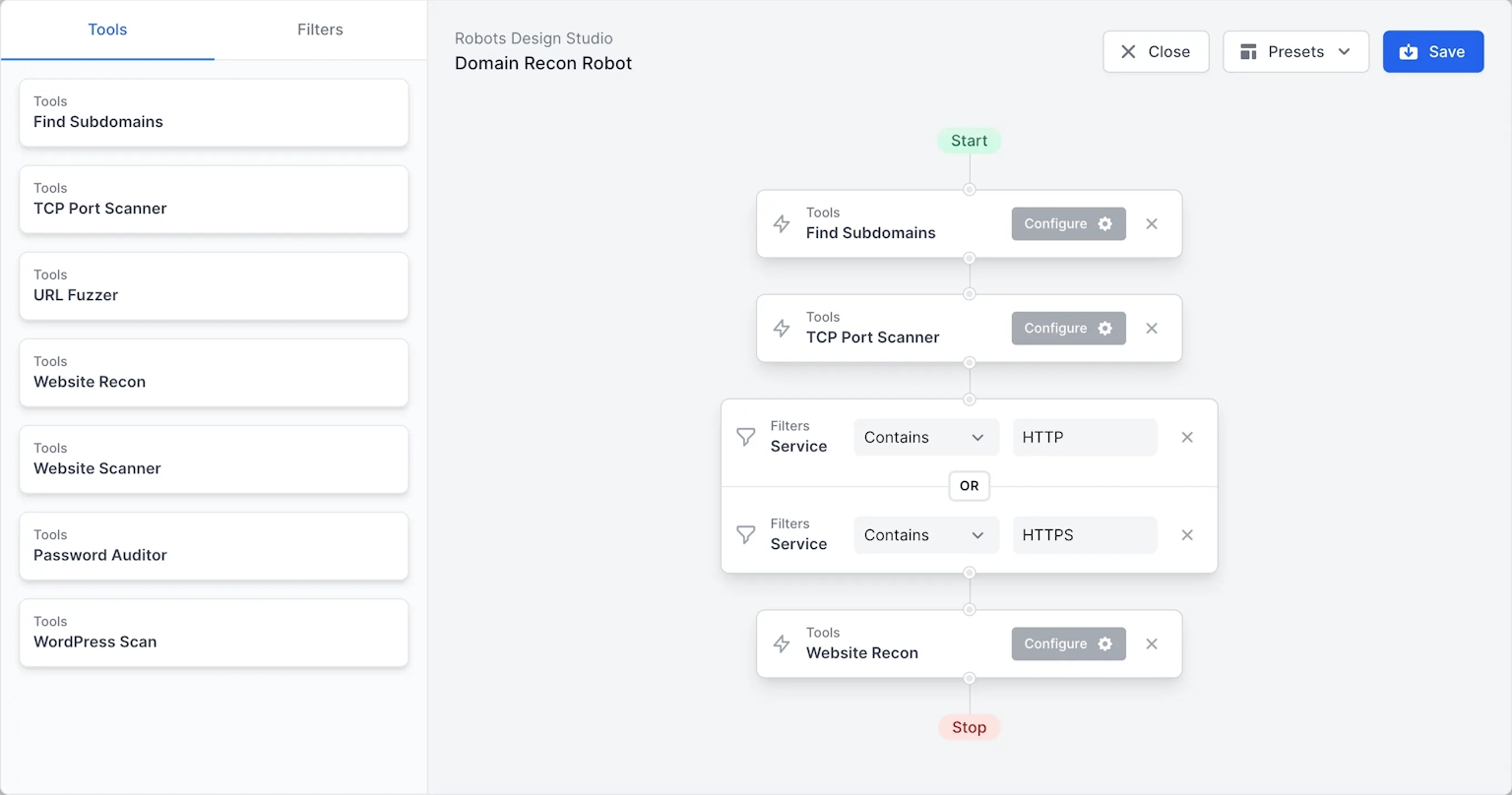
Recon Robot
Discovers all subdomains of a target domain. Then continues with full port scanning and service discovery.
For each web port, it does recon to gather technologies and take screenshots. You can find all the data aggregated in the unified Attack Surface view.
Web Login Bruteforcer Robot
Identifies all the web ports of the target host.
For each web port (80, 443, 8080, 8443, etc.), it runs the URL Fuzzer using a list of common web interface URLs.
For each login interface found, it runs the Password Auditor to find weak, common credentials.
Tools
Port Scanner
Filters
Service
Tools
URL Fuzzer
Filters
URL Found
Filters
URL Found
Filters
URL Found
Tools
Password Auditor
Deep Web Scanner Robot
Identifies all the web ports of a target host (80, 443, 8080, 8081, anything which speaks http/s).
For each web port, it does a full Website Scan, searching for:
Before it wraps up, this pentest robot produces an aggregated report with all the findings.
Want more robots?
You can assemble your own in seconds by using our logic blocks and chaining them together however you see fit!
Why don't you take your first Pentest Robot for a spin?
Trusted by experts at






























Testimonials
How security & techpros use the platform
At first we thought you were planning to leave us pentesters without a job and replace us with robots. But, joking aside, we believe this feature can indeed help us automate manual tasks and save time. Seeing how intuitive it is and how it provides a clear audit trail showed me it is very promising if further improved. It looks great and we can't wait to use it at full potential!
Start using the platform today
Unlock the full power and features of our platfom!
Compare pricing plans and discover more tools and features.
FAQ
Common questions
To build your first pentest robot, log into your Pentest-Tools.com account and go to the Robot Design Studio. Combine tool blocks with logic blocks to design the visual penetration testing flow that fits your specific needs.
To scan with your pentest robot(s), go to Targets, select the one(s) you want to Scan with Robot, choose the pentest robot you want to use and click on Start Scan. Yes, it’s that easy!

