Proof-driven network penetration testing
Run expert-level network penetration tests across external and internal network assets with proprietary capabilities designed for faster workflows, real exploitation data, and zero compromise on depth or control.
Get highly accurate validated findings with confirmed exploits and structured vulnerability evidence.
Chain together attacker-like, multi-step testing sequences with pentest robots.
Prove real risk instantly using Sniper’s custom-built exploitation modules.
Cut false positives fast with real exploit validation, ML filtering, and continuously updated detection logic.
Watch the demo
Speed up tedious manual pentesting steps, surface critical findings, and connect the dots into real attack paths.
Learn more about our tools with an in-depth walkthrough of the Pentest-Tools.com network pentesting capabilities in action.

Test your infrastructure faster. Prove more. Stay in control.
A cloud-first toolkit optimized for resource-intensive network pentests
We cover your whole pentesting cycles from recon to reporting, so you can focus on finding and proving high-impact security issues. No tool sprawl, and no setup delays.
Get full control, flexibility included
Customize how tools run to match your approach. Choose specific tests, configure wordlists, control scanning depth, and prove risk with precise penetration testing tools. The intuitive interface lets junior testers contribute early, while experienced teammates stay in control of methods and execution.
Eliminate false positives fast
Cut through noise with automated attack surface mapping that draws from multiple vulnerability scanners. Every validated finding includes the evidence you need to build a proof of concept or take immediate action.
Do work that flows naturally
Integrate advanced pentesting directly into your workflows with our flexible API. Build custom pipelines, trigger exploits using live asset data, or automate testing in CI/CD for new environments.
Pentest-Tools.com is with you at every stage of your network penetration test
With Pentest-Tools.com, you’ll gain a toolkit that boosts every stage of your network assessment:
Recon: Domain Finder, Subdomain Finder, Virtual Hosts Finder, Port Scanner, and more.
Vulnerability scanning: Network Scanner, Kubernetes Scanner, Password Auditor and more.
Vulnerability exploitation: Sniper: Auto-Exploiter, SQLi Exploiter, XSS Exploiter, HTTP Request Logger and more.
Attack surface mapping for a global view of potential infiltration points an attacker can use
Customizable, automatically generated pentest reports(.DOCX, PDF, HTML) to present your findings with more proof.
Spend less time on repetitive pentesting tasks and more time breaking things creatively.
Zoom in with deep recon
Find vulnerable subdomains, associated files, and expose potential entry points of the attack surface with Port Scanner, Subdomain Finder, and Cloud Scanner. Detect vulnerable services like exposed Exchange Servers, Confluence instances, misconfigured S3 buckets, and more.
You'll need:
Pentest your internal network’s vulnerabilities with a VPN agent
Our VPN Agent enables you to scan internal networks and run comprehensive penetration tests remotely via a secure VPN tunnel, without performing any special configuration.
Discover critical vulnerabilities like missing security patches, outdated network services, open ports, exploitable software, and weak credentials, from the get-go.
Test internal networks as if you were on-site, deploying your full arsenal to understand your target's attack surface.
You'll need our VPN Agent.
Prove risk instantly
Detect over 21,000 CVEs and collect key details (banners, configurations, and version data)with the Network Vulnerability Scanner.
When high-impact vulnerabilities are found, Sniper Auto-Exploiter safely validates them through real exploit attempts, allowing you to perform limited tests without altering production. It then delivers proof: screenshots, raw payloads, request/response logs, and post-exploitation output.
Use the Password Auditor after to quickly test for weak or default credentials across internal assets. No setup, no guesswork, just validated results you can act on.
You'll need:
Match findings with high-value penetration testing reports
Deliver actionable, evidence-rich findings through the pentest reporting tool, complete with exploit validation, screenshots, and request/response payloads that demonstrate proof of concept.
Generate fully customizable DOCX reports tailored to your internal structure or compliance frameworks, and export findings as CSV or structured JSON to feed results directly into your clients’ ticketing systems, dashboards, or other tooling ecosystems.
Contextual risk information is paired with embedded remediation guidance to help technical teams respond with speed and precision.
Replicate your winning workflow
Mix continuous monitoring with regular, point-in-time testing to cover all bases.
Set up scheduled scans, keep an eye on changes with built-in monitoring, and easily adapt your process: tweak finding templates, reuse engagement formats, fine-tune report styles, and run multi-step testing sequences with pentest robots and custom wordlists.
Want everyone in the loop? Connect your tools with Jira, Slack, Discord, Vanta, webhooks, and many more integrations.
How customers use Pentest-Tools.com for network pentesting
We work with security consultants, internal teams, and MSPs (some solo, some in big teams) and we know every pentest looks a little different.
Our CEO is a vetted pentester himself, and even our own Services team uses the product in real client engagements. This hands-on experience shapes everything we build.

Get solid proof and accurate results
The most helpful thing about Sniper is to know I can quickly validate critical vulnerabilities for customers and show them how malicious actors can exploit it. Reliable proof-of-concepts help the client understand the risks of vulnerabilities found and urge remediation.
Another aspect I enjoy is the ease of use and how I can perform limited tests (without altering the production) and get solid proof and accurate results. It saves tons of time and the burden of manually exploiting vulnerabilities.
Daniel Tomescu - Ethical hacker and Senior Manager
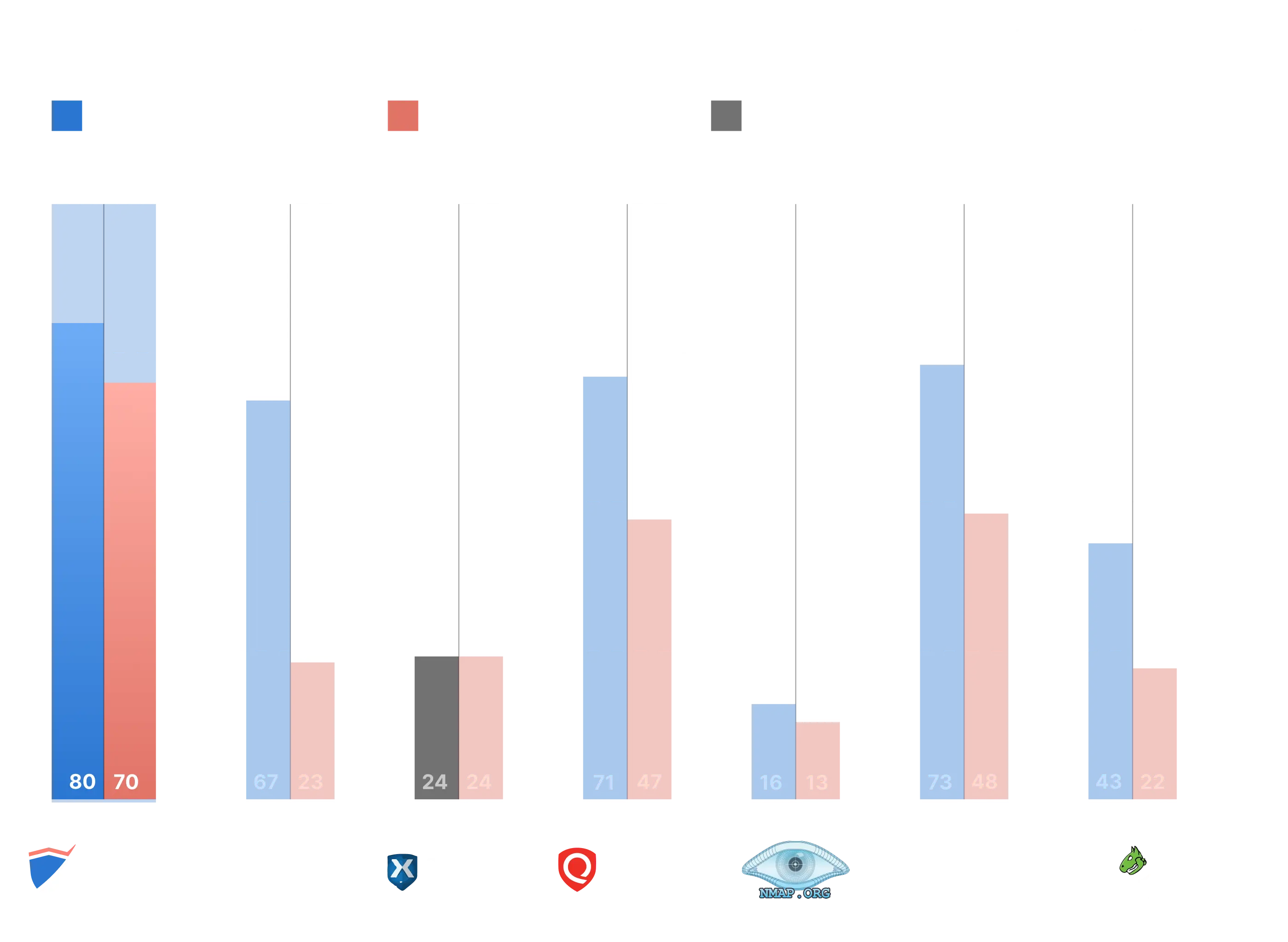
Outperforming top scanners in real-world detection tests
We put our Network Vulnerability Scanner to the test in a rigorous benchmark against seven leading network scanners, focusing exclusively on 128 live environments with remotely detectable CVEs. While we initially identified 167 potentially vulnerable setups, we excluded those that required local exploitation to ensure the comparison reflected real-world remote scanning capabilities.
The result? It ranked #1 in overall detection performance, outperforming both commercial and open-source tools.
Network vulnerability scanners benchmark
See how one of our customers' favorite tools stacks up in the full detection benchmark, and explore how accurate detection leads to faster, more confident remediation.
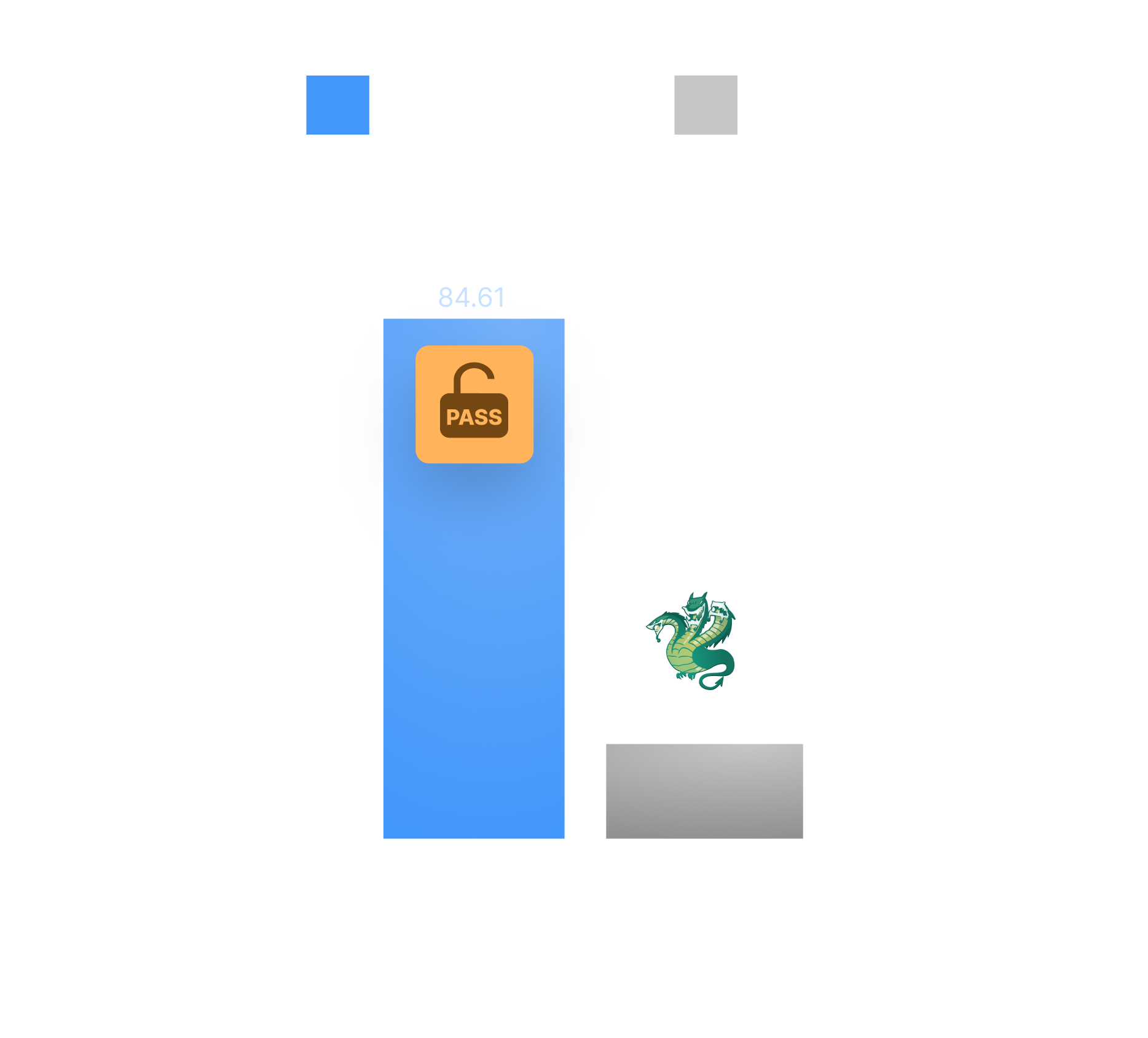
Brute-force battle: our Password Auditor vs Hydra
This comparison puts Hydra and the Password Auditor to the test across 26 web applications - including Microsoft Exchange, WordPress, and Joomla - to evaluate how effectively they identify weak credentials, navigate complex login forms, and detect security defenses like CAPTCHAs and IP blocking.
See the real proof for both performance and for the reports you need to ship!
Validate real risk. Start pentesting your network now.
From recon to reporting, comb through targets to find hidden vulnerabilities, missing patches, and misconfigurations with our extensive Pentest-Tools.com network penetration toolkit.
Why use Pentest-Tools.com for your network pentests
20+ tools for efficient, in-depth network and web pentesting
Options for comprehensive recon & deep, internal scans through VPN
Unified management for assets, findings & reporting at workspace level
Pentest robots for custom, automated testing flows that respect expertize
API access for large-scale scanning, dashboard integration & more
Cloud-first product optimized for resource-intensive network scans
Up-to-date Vulnerability & Exploit database with 21,000+ security issues
Fresh security research unpacking new exploits, attack techniques & more
Shared workspaces for extra visibility and team collaboration
Scheduled scans & custom alerts for recurring network pentest workflows
Network penetration testing resources

Need a full-service, manual network pentest?
Our team of seasoned offensive security experts delivers custom penetration testing and red teaming services built around your infrastructure, compliance goals, and business needs.
FAQs: Pentest-Tools.com for network vulnerabilities assessments
Why should I use Pentest-Tools.com for my network pentests instead of other products?
We build Pentest-Tools.com to amplify your abilities and know-how, not replace them.
Unlike many products that stop at detection, Pentest-Tools.com supports automatic proof-of-exploit capture, including request/response payloads and screenshots.
This helps security engineers to validate vulnerabilities more easily and include necessary evidence in audit-ready reports - reducing manual work for teams with strict internal controls.
How do I know if my network is vulnerable?
Run a thorough scan and receive a detailed report that unveils potential vulnerabilities - key insights into the entry points attackers hackers might exploit for infiltrating a network, exfiltrating confidential data, and delivering other types of threats.
Need expert guidance in evaluating your attack surface, identifying vulnerabilities, and fixing misconfigurations? Our certified penetration testing service team is here to help.
How do I scan for network vulnerabilities?
Take your pick: go for a free scan or level up with one of our premium plans for the full power of our Network Vulnerability Scanner, plus 20+ tools and a range of features to supercharge your pentesting process.
For a hands-on walkthrough, explore our guide on conducting a thorough network vulnerability assessment using Pentest-Tools.com.
What’s the difference between Sniper Auto-Exploiter and the Metasploit framework?
Each of the Metasploit modules must be configured manually, unlike Sniper where you just need to enter an IP / Hostname.
In Metasploit, if an exploit is successful, you get an interactive session where you can send commands to the target.
This contrasts with Sniper Auto-Exploiter, where the exploitation part is safely controlled by the tool, which executes predefined commands to ensure the target system is left in a good state after exploitation.
How does Sniper Auto-Exploiter work with the Network Vulnerability Scanner?
Among its extensive detection capabilities, our Network Vulnerability Scanner also incorporates Sniper exploitation modules. This gives you the ability to detect the latest critical vulnerabilities and the option to validate them through automatic exploitation with Sniper as a standalone tool.
The Network Vulnerability Scanner only uses detection capabilities that come from Sniper modules.
What information does a penetration test report include?
Each pentest report you automatically export from Pentest-Tools.com includes all the information categories any penetration test report should include.
These report sections are must-haves for any professional pentest report:
Introduction
Methodology
Background
Disclaimer
Objectives
Executive summary
Scope
Findings & Remediation
Approach
Addendum.
You also have the option to manually add findings you got from other scanners or manual work, so you’re not bound to our scanners’ results.
How is the Network Vulnerability Scanner different from the open-source versions of Nuclei and OpenVAS?
Our scanner uses proprietary enhanced versions of both tools. For Nuclei, we’ve improved detection coverage on specific templates, and built fully custom ones in-house. Findings are enriched with custom vulnerability descriptions, risk insights, and remediation steps.
For OpenVAS, we apply detection quality filtering to reduce noise, excluding templates known to generate false positives.
Find real risks, real fast, with the right Pentest-Tools.com plan
Choose the plan that powers every stage of your network pentest - from fast recon and real exploit validation to automated reporting and continuous monitoring.
Uncover critical network risks in minutes and report with clear-headed confidence.









![Network vulnerability scanners benchmark [2024] - methodology & results](/_vercel/image?url=https:%2F%2Fcontent.pentest-tools.com%2Fassets%2Fcontent%2Fns-benchmark---yt-thumbnail.png&w=1536&q=100)