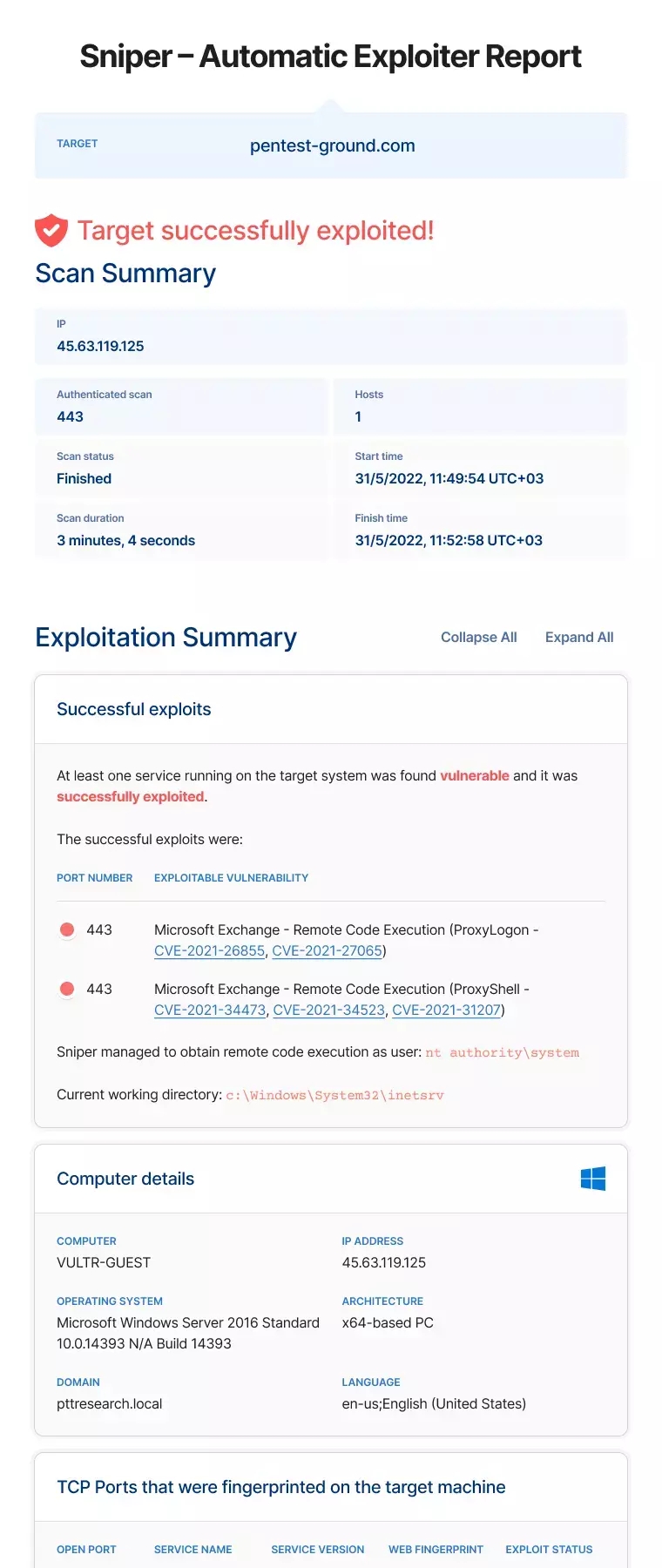
Sniper – Automatic Exploiter
Technical details
We initially developed Sniper to bridge the gap between results that common vulnerability scanners produce (e.g. Nessus, Qualys, OpenVAS) and the attack methods real threat actors use. While vulnerability scanners generate a high volume of potential issues, which also include a lot of noise and false positives, real attackers frequently focus on a few, highly effective, and targeted intrusion techniques.
Adversaries have plenty of opportunities to do this by using the constant stream of high-risk, high-impact vulnerabilities. To help offensive security specialists cope, we enhanced Sniper with capabilities designed to help them react with precision and speed in time-sensitive situations.
Sniper is a custom vulnerability exploitation tool that simulates exploits and attack techniques – which adversaries use in real world scenarios – to determine which systems are truly vulnerable. It offers both remote (unauthenticated and authenticated scan options) and client-side attacks, with the ability to extract data from the target as an adversary with access to login credentials.
After successful exploitation, Sniper automatically runs post-exploitation modules that extract interesting data from the target system as solid proof of successful intrusion. We call this data artefacts and the list includes:
- Current user (e.g.
nt authority/system) - Current directory ( e.g.
C:\Program Files\Apache Software Foundation\Tomcat 9.0) - System information (e.g. operating system, equipment type and version, software type and version, running applications, architecture, hotfixes, etc.)
- List of local users with privileges on the target machine, together with password hashes, if the current user has a privileged account
- List of running processes, including full paths for each executable
- Visual summary of the network configuration that offers rich and actionable context
- Network neighbors (live hosts) from the same local area network as the target host
- Network connections with their communication protocols
- Network services with open TCP ports.
Security teams and independent specialists can use all this data to continue their pentesting work with manual methods for reconnaissance, lateral movement, and pivoting to sensitive and important targets. The automatically generated network graph is particularly useful to navigate complex infrastructures, as it eliminates the need to spend time correlating information.
When Sniper succeeds in exploiting a vulnerability, it validates the risk is real and attackers can exploit it at any given moment, indicating that system administrators must act straight away.
Using Sniper as your vulnerability exploitation tool helps you become very effective at filtering out the noise that vulnerability scanners create, eliminating false positives, and helping you focus on the vulnerabilities that matter. Here's how many of them we detect compared to other security platforms like Detectify or Invicti.
Exploit modules
Below you can see a shortlist of modules that Sniper currently uses to automatically exploit known critical vulnerabilities in high-profile software and get you proof of compromise.
| Name | Detectable with | Detection added | Severity | Exploitable with Sniper |
|---|---|---|---|---|
| Magento & Adobe Commerce - Account Takeover | Network Scanner | Oct 15, 2025 | Yes | |
 FreePBX - Authentication Bypass leading to SQL Injection & Remote Code Execution FreePBX - Authentication Bypass leading to SQL Injection & Remote Code Execution | Network Scanner | Sep 30, 2025 | Yes | |
| Fortinet FortiSIEM - Remote Code Execution | Network Scanner | Sep 9, 2025 | Yes | |
 Microsoft Sharepoint - Authentication Bypass & Remote Code Execution Microsoft Sharepoint - Authentication Bypass & Remote Code Execution | Network Scanner | Sep 9, 2025 | Yes | |
| SSH user enumeration | Network Scanner | Aug 19, 2025 | Yes | |
 Ivanti Endpoint Manager Mobile - Remote Code Execution Ivanti Endpoint Manager Mobile - Remote Code Execution | Network Scanner | Jul 1, 2025 | Yes | |
| Wordpress TemplateInvaders - Arbitrary File Upload | Network Scanner | Jun 24, 2025 | Yes | |
 Craft CMS - Remote Code Execution Craft CMS - Remote Code Execution | Network Scanner | Jun 2, 2025 | Yes | |
| SMB - Anonymous Write Access | Network Scanner | May 20, 2025 | Yes | |
| SMB - Anonymous Access | Network Scanner | Apr 29, 2025 | Yes |
You can click here to browse the complete database of vulnerability detections and exploitable vulnerabilities.
As you can see, many of these CVEs are also part of CISA’s Known Exploited Vulnerabilities Catalog, which indicates they are under active attack. Our dedicated security research team focuses on integrating exploitation and post-exploitation capabilities for new CVEs as they emerge, as we are fully aware of the time-sensitive nature of these vulnerabilities.
We constantly update this list with new critical CVEs and you can find out the moment they’ve live:
Artefacts for vulnerability validation
Artefacts are data from the target system which Sniper automatically extracts after one of the exploits succeeds. They provide solid proof that the target is vulnerable and support security specialists with further manual exploitation, if necessary.
Sniper Auto-Exploiter extracts artefacts by running predefined shell commands on the target, depending on its operating system. For instance, to extract the current user on a Linux system, the extractor will run the command whoami whereas on Windows it will run the command net user.
This is the list of artefacts that Sniper extracts:
| Artefact | Description |
|---|---|
| Current user | The name of the current system user that the exploit code is running as (e.g. root, Administrator or www-data). |
| Current directory | The name of the directory that the exploit code is running as ( e.g. /var/atlassian/confluence or C:\Program Files\Apache Software Foundation\Tomcat 9.0 ) |
| System information | Information about the operating system like OS type, version, kernel, processor architecture, memory size, hotfixes, etc. |
| List of local users | A listing of the users currently configured on the operating system (e.g. from /etc/passwd file or from net user command), along with their password hashes, if the system user has administrative privileges. |
| List of running processes | A listing of the operating system processes that are currently running on the target system. |
| Network configuration | The settings of the network interfaces of the target machine (e.g. IP address, network mask, default gateway, etc.) |
| Network neighbors | A list of live hosts from the same local network as the target (layer 2). |
| Network connections | The list of open ports and established TCP connections of the target to other systems in the network. |
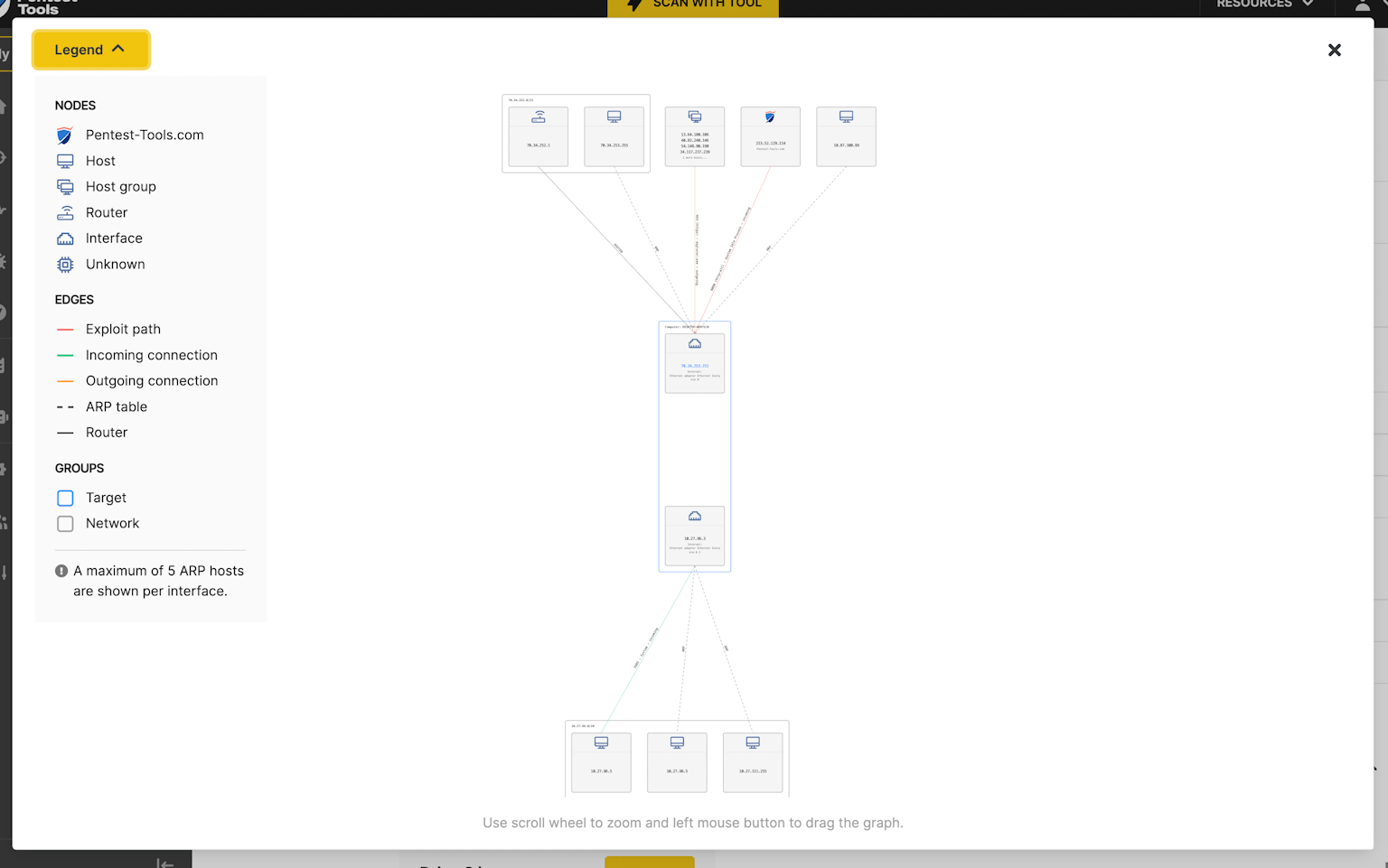
Sniper network graph - explore the visual summary
Understanding the network architecture behind the exploited host is an essential step for both offensive and defensive information security specialists. So we built this capability into Sniper Auto-Exploiter with the visual summary section in the tool results.
The visual summary feature in Sniper results helps you instantly visualize the network configuration of your target host. Explore the automatically generated network graph to see:
- All TCP connections (inbound or outbound) between your target and other hosts on the network (routers, workstations, etc.) and their system information
- Interfaces configured on the exploited host
- The exploit path(s) which Sniper used to safely compromise the machine
- Communication protocols for each connection (SSH, HTTPs, HTTP, ms-wbt-server, etc.)
- A list of adjacent hosts from nearby network subnets
- ARP routes and host groups, especially helpful for multiple targets that communicate on the same port with the exploited target.
The Sniper network graph pulls data from the artefacts it extracts and automatically correlates the network information when the tool gains RCE on a target. With this feature, Sniper removes time-consuming manual work, gives you the big-picture context of your target, and frees up your schedule for more stimulating work.
With the elements of your target’s network topology already arranged for you, you can identify top targets to pivot to much faster as a red teamer. If you’re on the blue team, Sniper’s network graph helps you discover all unknown connections originating from your target and to it. With this information, you can audit these connections to determine if the system has been exploited before and if it has a backdoor connection to malicious endpoints.
This visual representation of the target’s Network architecture makes it easy to understand how systems are connected, even for complex infrastructures. It also highlights the impact of a vulnerability, offering persuasive proof for peers in security and IT, but also to decision-makers in other business units.
For example, the Sniper network graph helps you see if multiple targets communicate on the same port with the exploited target, essentially opening them up to malicious exploitation.
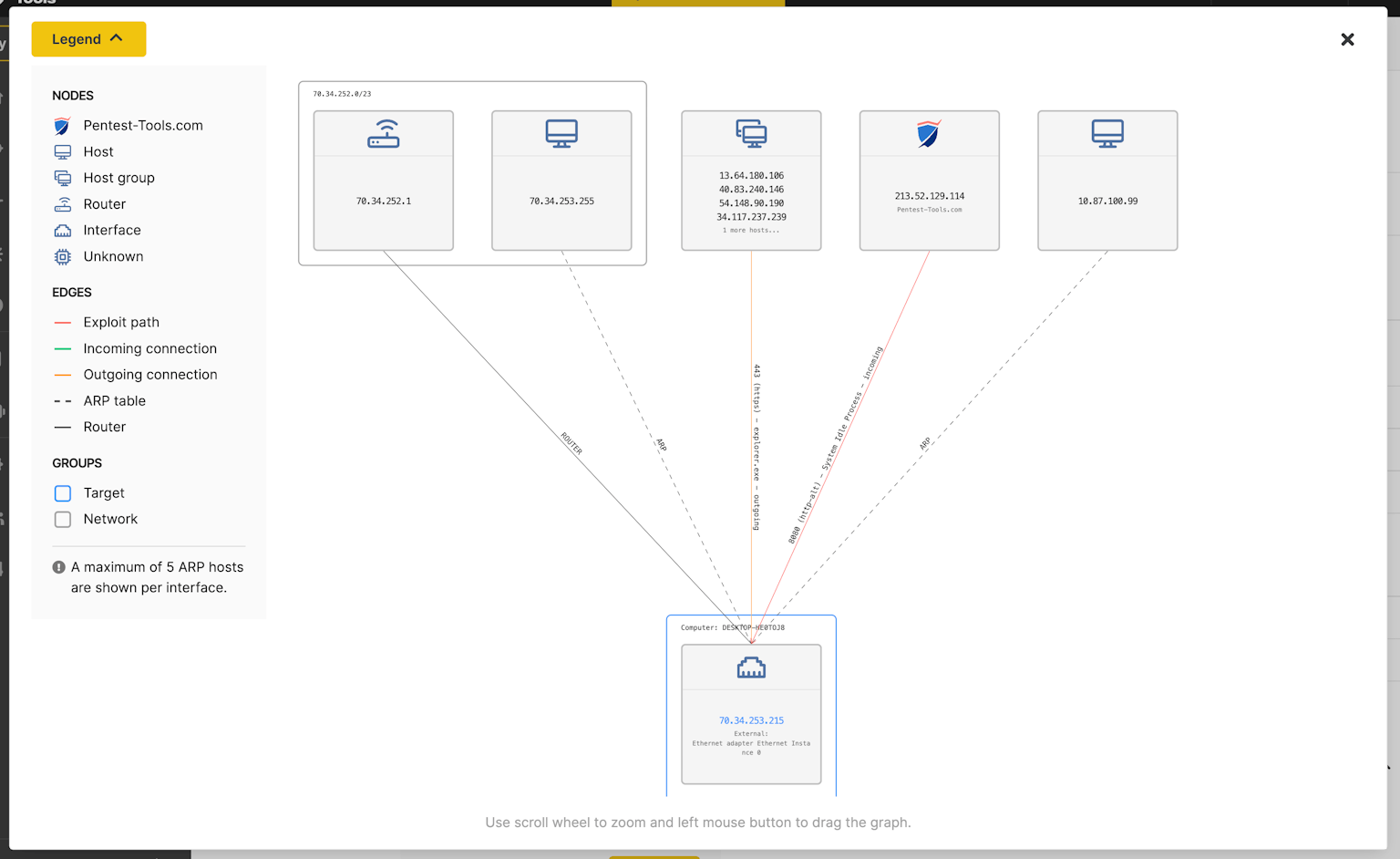
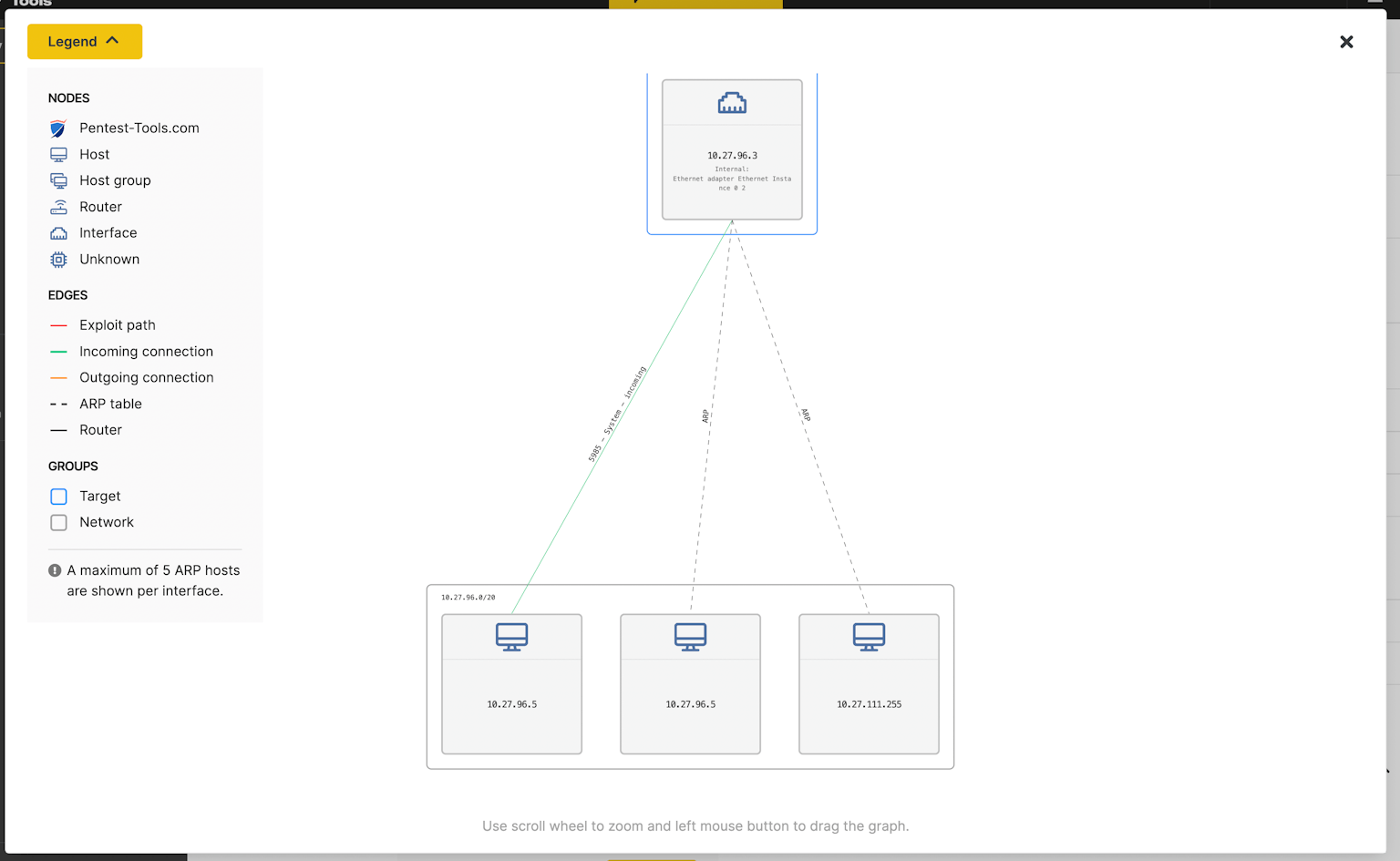
You can use Sniper to see the network topology after a successful automatic exploit and even after an authenticated scan, no matter the depth of your expertise in the field of networking. If you need this visual representation for any other system, you can also run Sniper against targets that aren’t vulnerable.
Sniper Auto-Exploiter currently supports SSH, WinRM, SMB, and MySQL scanning, and we continue to add options for our Pentest-Tools.com customers.
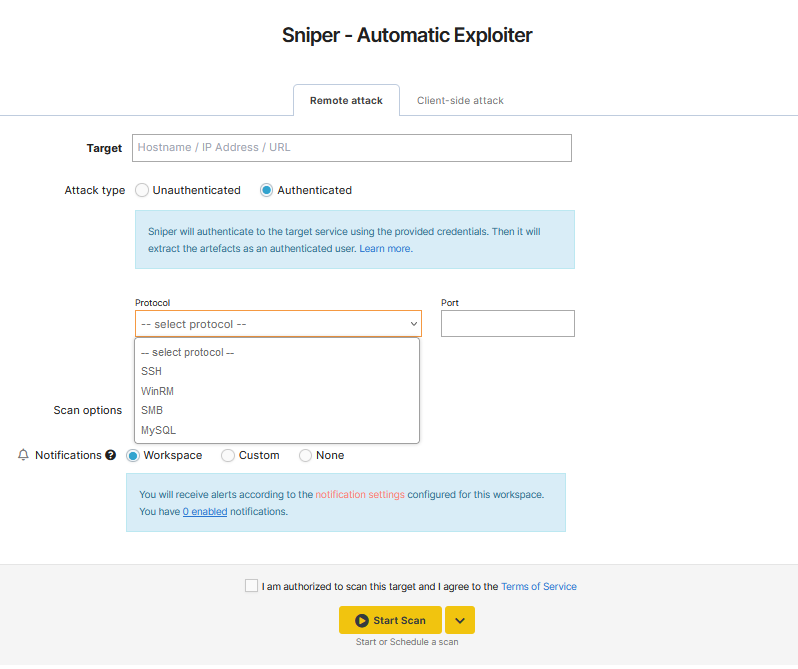
Scanning parameters for remote attacks
When you choose a paid plan and log into your Pentest-Tools.com account, you can select and combine the following scanning parameters for safe vulnerability exploitation with Sniper:
| Parameter | Description |
|---|---|
| Target | Specifies the system that will be scanned. Target can be an IP address, hostname or an URL. |
| Attack type | Selecting the unauthenticated scan option instructs Sniper to simulate an unauthenticated attack against the target and try to exploit any vulnerability it finds. Artefacts will be extracted after successful exploitation. Otherwise, during an authenticated scan, Sniper authenticates to the target service using the credentials you provide. Then it extracts the artefacts as an authenticated user. |
| Ports to scan | This option is available only for unauthenticated scans. These are the ports that Sniper will try to automatically fingerprint and attack. Can be specified as common ports, range, or list. |
| Protocol | This option is available only for authenticated scans. This is the protocol used for authentication. Available options: SSH, WinRM, and SMB. |
| Port | This option is available only for authenticated scans. This is the port used for authentication. |
| Username & password | This option is available only for authenticated scans. These are the credentials used for authentication. |
| SSH private key | This option is available only for authenticated scans, when the SSH protocol is selected. This is the SSH private key used for authentication. |
| WinRM authentication type | This option is available only for authenticated scans, when the WinRM protocol is selected. This is the authentication type ( NTLM / Basic ) used for authentication. |
| SMB authentication type | This option is available only for authenticated scans, when the SMB protocol is selected. This is the authentication type ( Local / Domain ) used for authentication. |
| Check if host is alive before scanning | Enables the check alive mechanism before searching for any open ports during the discovery phase. |
Information provided for client-side attacks
| Column | Description |
|---|---|
| Label | This is the identifier of the handler that also serves as the document’s name. |
| Targets | This shows how many victims opened the document and, when expanded, details about the victims (i.e. IP address). |
| Type | Shows the type of document that was created. Currently, the supported options are doc, .docm, .xls, .xlsm. |
| Status | Show days remaining until the handler expires and the status of each scan. |
| Start Time | Appears when the victim opens the document and the Sniper scan starts. |
What to do after running Sniper Auto-Exploiter
You can now chain our Network scanner finding that only detects a vulnerability with the Sniper Auto-Exploiter tool with a custom button called “Exploit with Sniper”.
Besides Sniper Auto-Exploiter, you have a full arsenal of reconnaissance, vulnerability scanning, and offensive tools on Pentest-Tools.com to carry out a thorough and effective security assessment.
You can chain findings from the Network Vulnerability Scanner, focused on detecting vulnerabilities, and use the “Exploit with Sniper” button to gain proof of compromise.
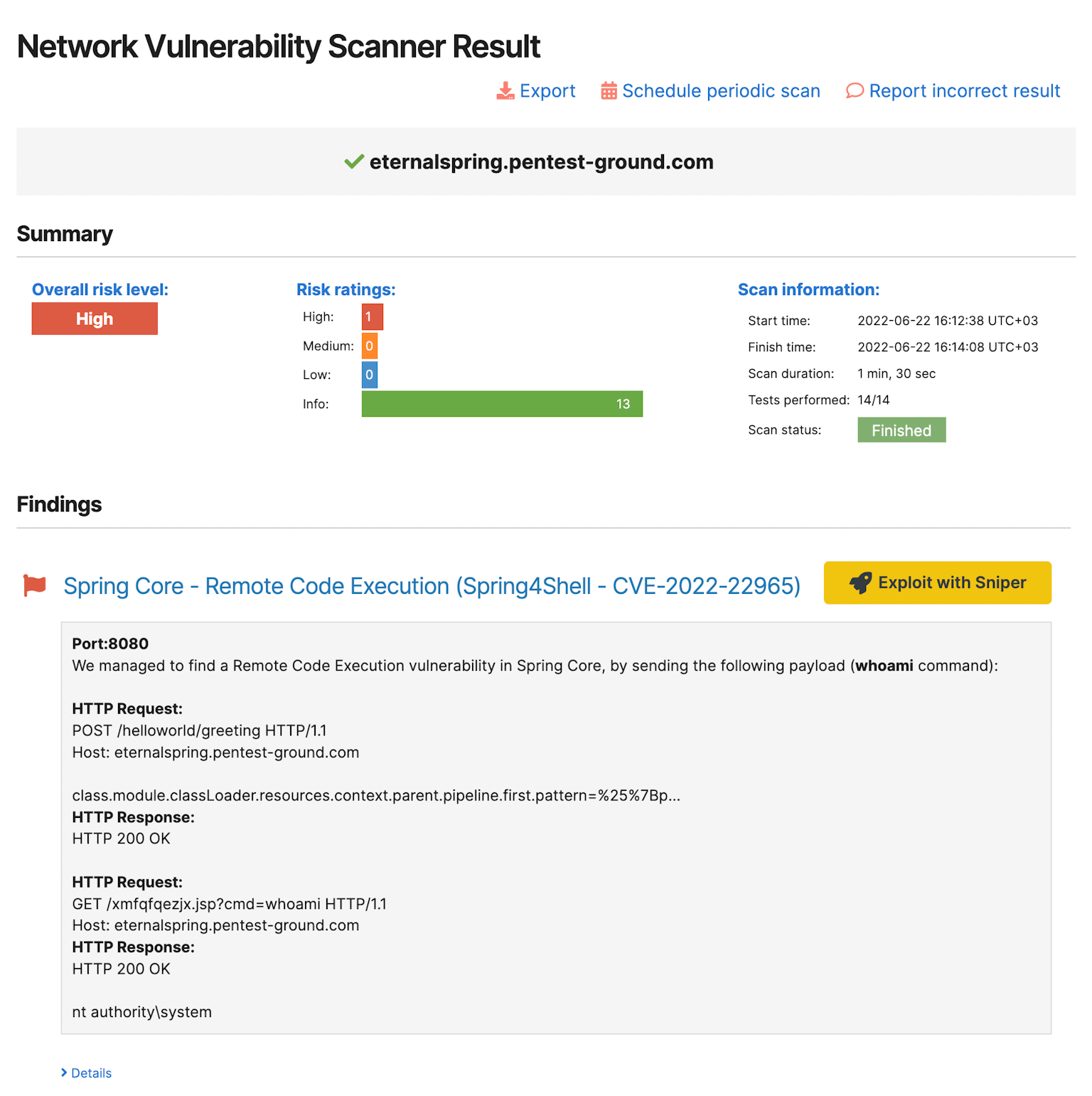
For example, if the Network Vulnerability Scanner finds that your application is vulnerable to the Proxyshell exploit chain, you can use the “Exploit with Sniper” button to go to the Sniper tool and quickly validate if it truly is vulnerable. At the same time, you gather important information about your system through the list of artefacts.
To save even more precious time, try out our ready-to-use scan templates which group multiple tools in one bundle, so you can launch them all at once. Scan templates are also customizable or you can build your own and reuse them to fine-tune engagements and do your best work.
With your Sniper results handy, you can start digging deeper and pursue the most interesting targets in it while also getting inspiration for lateral movement and ways to abuse business logic in your pentest engagements.