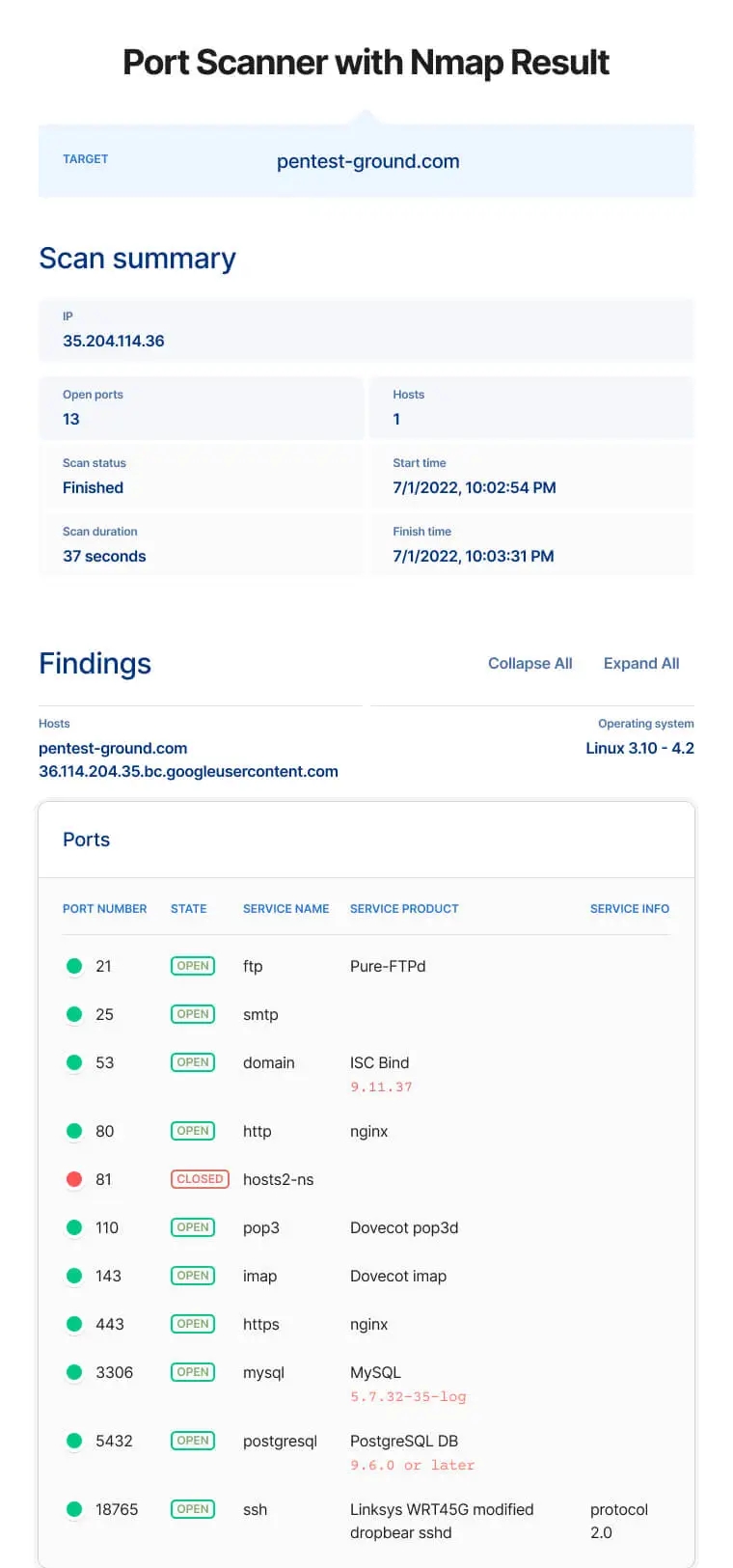
Port Scanner with Nmap
Technical details
What is a port scanner?
A port scanner is a software application designed to check open ports on a server’s IP address or hostname by sending probe packets to TCP or UDP ports and checking the responses. Find specific details about each port scanning method below.
Security and IT specialists use an open port scanner tool to check how security policies are implemented and make accurate recommendations to reduce risk.
Malicious hackers also rely on public port scanners to discover exposed and outdated network services they can exploit to gain unauthorized access to a target. This is why offensive security pros need reliable port scanning tools to keep ahead of remote attackers and proactively reduce risk.
Why use an online port scanner at all?
The main benefit of using an online version of the Nmap port scanner (vs using it on your local machine) is that it gives you an external view of your systems as any malicious hacker from the Internet has. If you do the same scan from your internal network you may obtain different results because of various firewalls and network restrictions. Furthermore, our port scanner is:
- Already configured and ready to run
- Periodically upgraded
- Has an easy-to-use interface over the complex command line parameters of Nmap
- Gives you a useful report that you can share with management or stakeholders
The scanner allows you to easily map the network perimeter of a company, check firewall rules and verify if your services are reachable from the Internet. Based on Nmap Online, it performs accurate port discovery and service detection.
What makes our Port Scanner with Nmap different
Nmap is the de-facto tool for finding open ports and services due to how effective it is. However, it takes a lot of manual work to use the Nmap at peak potential from the command line. That’s because it has lots of parameters and options that need to be well understood from the documentation.
That’s why we built an online port scanner on top of Nmap that comes pre-configured and always up to date. We handle performance and speed improvements so you can focus on using the results you get from our TCP and UDP open ports scanner.
Because it’s integrated into the Pentest-Tools.com cloud platform, this online port checker gives you rich options to continue your engagement. Reliable and easy to use network vulnerability scanners, web vulnerability scanners, offensive security tools, and automation features (e.g. attack surface mapping) are one click away and provide support for your entire penetration testing workflow.

The Light Scan version – free port scanner optimized for speed
Need an IP scanner online that doesn’t cost anything to use? You can scan ports for free twice a day for a single IP or hostname.
This open port scan we provide on the house checks for the Top 100 TCP and UDP ports and also reports the running services’ versions (-sV is enabled in scan configuration).
Top 100 TCP and UDP ports
7, 9, 13, 21-23, 25, 26, 37, 53, 79-81, 88, 106, 110, 111, 113, 119, 135, 139, 143, 144, 179, 199, 389, 427, 443-445, 465, 513-515, 543, 544, 548, 554, 587, 631, 646, 873, 990, 993, 995, 1025-1029, 1110, 1433, 1720, 1723, 1755, 1900, 2000, 2001, 2049, 2121, 2717, 3000, 3128, 3306, 3389, 3986, 4444, 4899, 5000, 5009, 5051, 5060, 5101, 5190, 5357, 5432, 5631, 5666, 5800, 5900, 5985, 5986, 6000, 6001, 6646, 7070, 8000, 8008, 8009, 8080, 8081, 8443, 8888, 9100, 9999, 10000, 32768, 49152-49157
As you can see in the list above, this free Nmap scan online covers the most common TCP and UDP ports:
- 21 - FTP (File Transfer Protocol)
- 22 - SSH (Secure Shell)
- 23 - Telnet
- 25 - SMTP (Mail)
- 80 - HTTP (Web)
- 110 - POP3 (Mail)
- 143 - IMAP (Mail)
- 443 - HTTPS (Secure Web)
- 445 - SMB (Microsoft File Sharing)
- 3389 - RDP (Remote Desktop Protocol).
The Deep Scan version – ready-to-use Nmap online scanner
The Deep version of our Port Scanner allows you to probe for open ports with custom parameters that you can easily customize from your cloud account.
Ports to scan options:
- common TCP and UDP ports (top 10, top 100, top 1000, top 5000)
- port range (1-65535)
- custom port list (22, 80, 443, 5060) for focused online portscans.
Scan for open ports options:
- enable or disable service version detection
- enable or disable operating system detection
- do traceroute
- enable or disable check if host is alive before scanning.
The Port Scanner in our cloud platform gives you two options: either approach your target as an external attacker would or do port scans directly against your services, as if the firewall has already been bypassed. The resulting Nmap scan report gives you the chance to identify and fix the root causes of security risks your target presents.
To get both perspectives and form a comprehensive view of all that target’s open ports, use separate workspaces – one without and one with our ready-to-use VPN agent. Alternatively, whitelist Pentest-Tools.com to gain full visibility into your target.
Let’s unpack how our ready-to-use online Nmap scanner works in three stages to achieve its goal:
1. Nmap host discovery
The scanner attempts to check if the target host is live before probing for open ports. This is essential for optimizing the scan duration when running the online IP scanner against a large range of IP addresses. It would be a waste of time to probe for open ports on a 'dead' host (e.g. there is no server at a given IP).
However, host 'liveness' can’t always be correctly detected. Causes include firewalls which allow access only to a certain port and drop everything else. So you might not find any open ports because of this. In this situation, whitelist our scanners or disable the “Check if host is alive before scanning” option to skip the host discovery phase and jump directly to the check all ports step.
2. Open ports detection
To determine if a TCP port is open, Nmap takes advantage of the Three way handshake mechanism used by TCP to establish a connection between a client and a server.
There are two main methods for detecting open TCP ports:
Connect-Scan (Nmap -sT)
Nmap does a full three-way handshake with the target server, establishing a full TCP connection. The sequence of packets for this type of scan is: SYN, SYN-ACK, ACK, RST.
This method doesn’t require root/administrator access on the client machine, but it’s rather noisy and the server can log the connections attempted from other hosts.
SYN-Scan (Nmap -sS)
This is the default scanning method, also enabled in our online open port scanner. Nmap does a half-open TCP connection, knowing the port is open as soon as the server responds with SYN-ACK. The sequence of packets in this case is: SYN, SYN-ACK, RST.
This method is stealthier than a Connect-Scan but it requires Nmap to run with root/administrator privileges, because it needs to create low-level raw sockets to send the individual packets, instead of leaving the kernel stack to do the connection.
3. Nmap service detection
Once Nmap finds a list of ports, it can do a more in-depth check to determine the exact type of service running on that port, including its version. This is necessary because common services can run on non-standard ports (e.g. a web server running on port 32566). Service detection is enabled with the -sV parameter.
Nmap does service detection by sending a number of predefined probes for various protocols to the target port and see if it responds accordingly. For example, it sends:
- SSL Client Hello to check for SSL services;
- HTTP GET request to check for HTTP service;
- SIP OPTIONS to check for SIP/RTSP protocol, and many others.
Besides accurate and fast port detection, other options in our cloud platform boost this scanner capabilities:
- Automatic Attack Surface mapping that pulls data from multiple pentest tools
- Scheduled scans and bulk scanning for continuous attack surface monitoring
- Real-time notifications through webhooks for uninterrupted workflows
- API access for ready-to-use scan engines
- Automation options such as pentest robots and scan templates
- Workspace & items sharing for effective collaboration.
What to do after running the Port Scanner with Nmap
After you check website open ports or do an IP port scan, you can act on the findings right from the list of results. A handy drop-down gives you the option to further scan open ports with various tools such as our Website Scanner, Network Vulnerability Scanner, URL Fuzzer, and Website Recon (for either URLs or IPs).
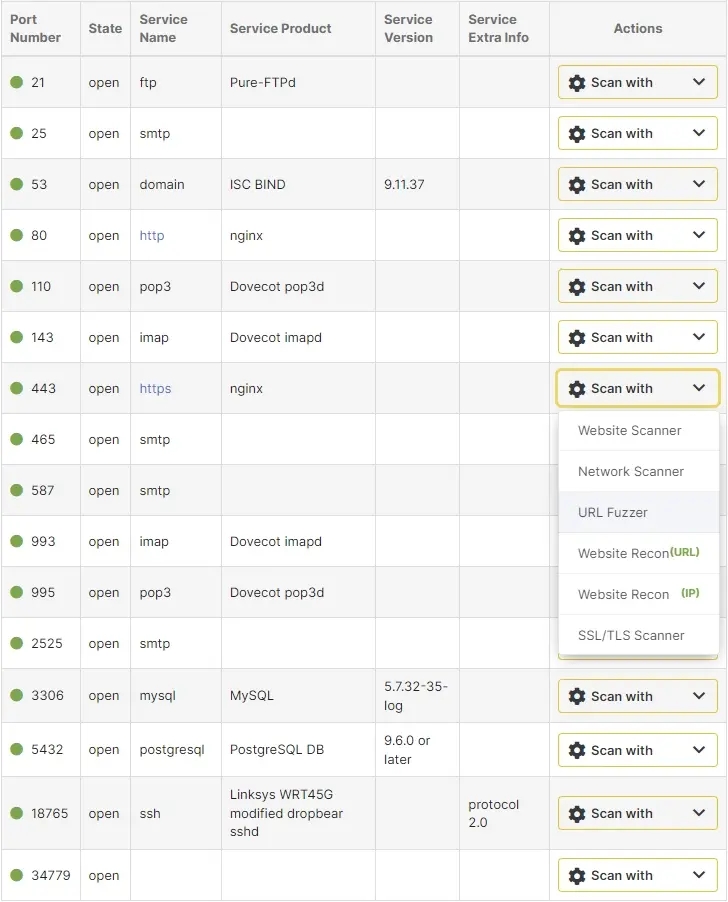
The arsenal of reconnaissance tools on our cloud platform also includes dedicated scanners that help you Find Domains, Find Subdomains, Find Virtual Hosts, find juicy information with Google Hacking, and perform a thorough UDP Port Scan.
To save even more precious time, ready-to-use scan templates which group multiple tools in one bundle sit at your fingertips. Just like scan templates, pentest robots are also customizable or you can build your own and reuse them to fine-tune engagements and do your best work.
For instance, this Recon Robot discovers all subdomains of a target domain and does deep port scanning and service discovery. For each web port, it does recon to gather technologies and take screenshots and delivers all the data aggregated in the unified Attack Surface view.
With your port scanner report, you can start digging deeper and pursue the most interesting findings in it while also getting inspiration for the next stages in your engagement, particularly around security issues related to business logic.